Table of Contents
Intro:
This quick article will touch on how to get started and perform SocGholish Research.
Purpose:
To find a way to hunt for SocGholish.
Reason:
You might be a new or aspiring SOC Analyst that wants to research malware, but you don’t know where to start.
You might be a SOC Analyst with friends and family that are curious about what you do, but you aren’t allowed to show them content from work because of privacy rules.
You might be a SOC Analyst that had a SocGholish alert at work, and you need to develop your own cyber threat.
Thanks:
Big mahalo to @monitorsg (https://infosec.exchange/@monitorsg) for pointing me in the right direction!
Mastadon post:
I saw that @monitorsg posts frequently about SocGholish and asked for help:
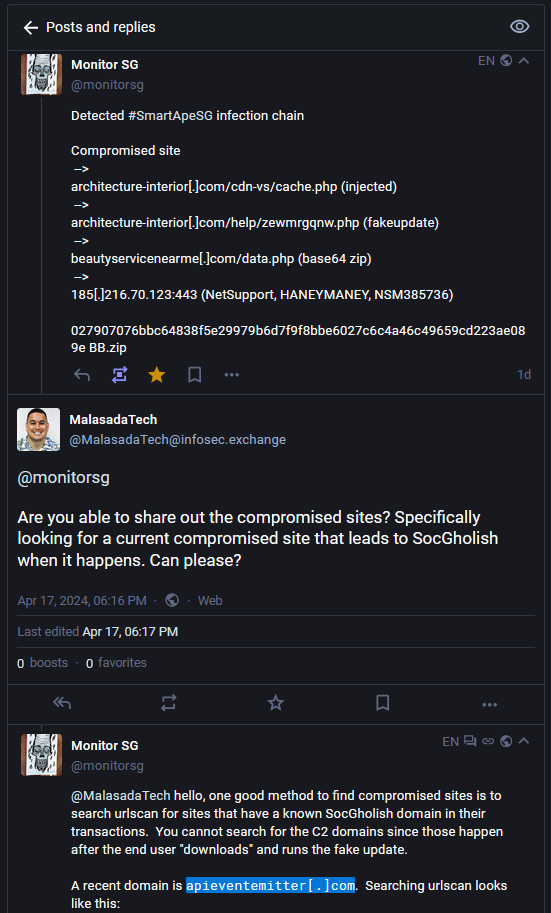
Super thankful for @monitorsg pointing me in the right direction!
urlscanio:
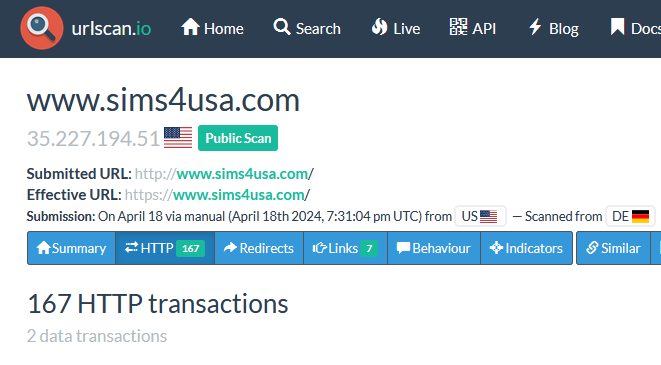
First search: domain:apieventemitter.com

Click the blue HTTP button and search for the related domain (apieventemitter)
Click the magnifying glass for the row to expand it:

You can click the Show response button to view the content:
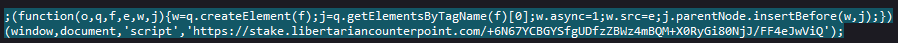
In the snip above we can see it appears to add a script call to the DOM.
We go back to the previous page that listed the HTTP requests and search for the request to libertariancounterpoint:
We see that it is a GET request that does not receive a response:
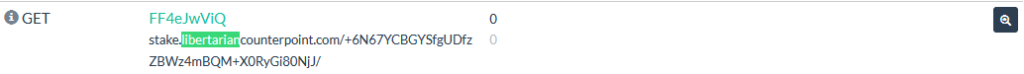
We also see that the bottom of the list shows us this was a failed request:

It’s ok. We return to the other row and click the resource hash:

This hash will show us the URLs that had a request for the same resource.

We tried to access sims4usa in Any Run, but was not served SocGholish. However, the Threats tab did show us the Suricata rule name “ET EXPLOIT_KIT TA569 Keitaro TDS Domain in DNS Lookup (apieventemitter .com)”

Emerging Threats:
We can take that and go to https://rules.emergingthreats.net/open/suricata-5.0/emerging-all.rules to find more info.
We see below that it is a recent rule created on 2024_04_11.

We search for the other rule and find the snip below:

We can see from that snip above that it is from 2024_02_21, and they reference @monitorsg’s Mastadon post. This is how I found @montorsg in the first place. I searched “SocGholish” in the rules list and saw the reference to @monitorsg.
It’s unfortunate that we didn’t get served the SocGholish fake update page in the Any Run session, but we’ll circle back to that later.
Summary:
You can hunt by monitoring @monitorsg’s feed, or the ET Rules List, for ParrotTDS, Keitaro TDS, or SocGholish, and then use urlscan.io to pivot for the compromised domains. You can then use those referrer domains to fishing for SocGholish.
Twitch Stream for this research: https://www.twitch.tv/videos/2123631975
TODO: Research ParrotTDS and KeitaroTDS.
