I spotted a lure masquerading as an Indeed Career Guide resource (https[:]//666025[.]xyz/erp-terms-of-contract). See below.
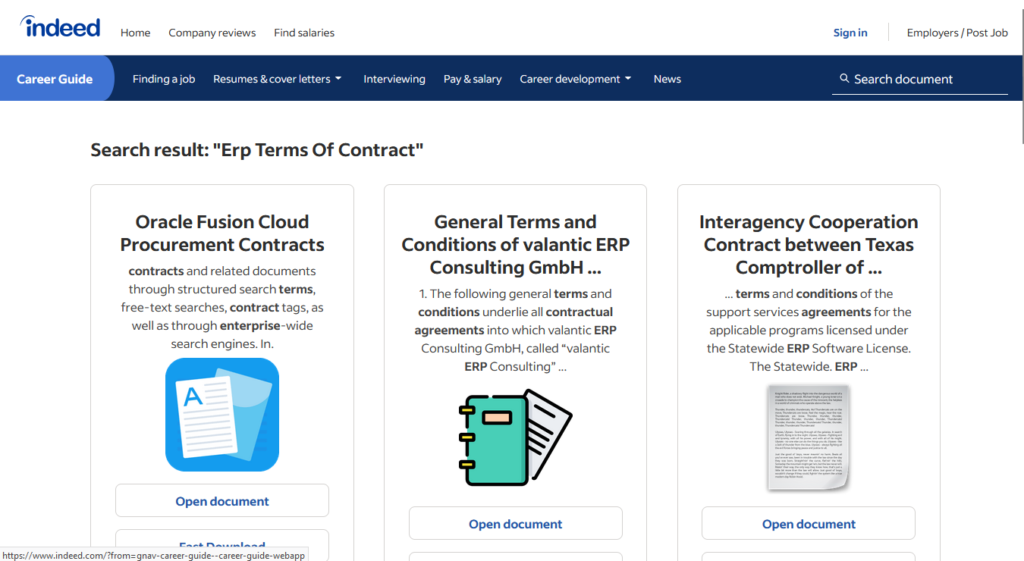
I found this while working on the Gootkit Crawler project – a project that will generate and execute search terms that will return Gootkit lure articles. I use something along the lines of: “site:*.(TLD) enterprise agreement”. I tried “site:*.xyz enterprise agreement”, and found the link to this.
I’ve previously observed this domain naming and lure style. It’s a big and notable one, but I don’t want to attribute it until I can be sure. There was another actor that I’ve been tracking, and it would be lovely if I could attribute this to them, but unfortunately I messed up on this investigation. Because I was just skimming and casually exploring Gootkit lures, I wasn’t mentally prepared for this. It sounds silly, but the excitement of recognizing this theme clouded my judgement and I think I made a critical mistake. Let’s get into it.
I hovered over the link, and took the snapshot below:

I messed up a few times because I was clicked into my VM, so when I pressed WIN+Shift+S it loaded the snip tool in my VM. My critical mistake (I think), was that I right-mouse clicked the link and click the context menu option to save the link instead of just clicking into it. From previous experience, if this is what I think it is, expressions.docx would not have been the actual malware. The DOCX file would have just been the second lure doc, and that would point to the actual malware.
By using multiple stages in the delivery, threat actors are able to filter out automated scanners. In this case, myjobsintanzania[.]com must’ve had some rule where it blocks my request because I clicked save as instead of directly clicking the link. The expressions.docx was an empty file. After this failed attempt, I tried to click directly into the link, and it forwarded me to a 404 page. I clicked the back button and realized my second critical mistake.
When I clicked the back button, it didn’t reload the lure page. It loaded a generic empty page. I lost my opportunity! I was too used to having PCAP available, that I didn’t think to save the lure HTML for further analysis. All of it was lost, and all I had left were these crappy snips.
I did a quick skim on accessing the Firefox cache and got into “about:cache”. It wasn’t the greatest, but I was able to find this:
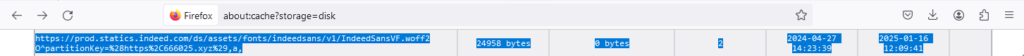
It isn’t much, but it is a threat hunting concept. The entry shows the partitionKey was from the lure domain 666025[.]xyz, and it shows it was an official Indeed resource from Indeed.com. I tried to find the image file for the Indeed logo:

I was unable to find it in about:cache – it isn’t the greatest resource, but at least we found the woff2 file. This is important because you can search for this activity (if you’re a SOC analyst), or similar activity. You would need to search for any request for a resource from prod.statics.indeed.com that was referred by a suspicious domain. For example, you could use the Splunk pseudo-query below to find .XYZ resources that are loading the Indeed resource:
* domain=prod.statics.indeed.com referer=*.xyz
| stats count by referer
Or, you could just remove the referer part for a bigger net.
I’ll keep retrying… hopefully I can get it again.