SEO Introductory Paragraph:
Discover how to automate the detection of Gootkit malware using urlscan.io. This detailed guide provides insights into using urlscan.io’s powerful API to identify malicious scripts and secure your digital environment. Learn how to enhance your cybersecurity measures with effective tools and Python scripts that streamline the process of detecting and analyzing potential threats online.
Table of Contents
Intro:
I thought it would be swell to create an article showing how urlscan.io could be used to find the forum loader scripts, to extract the mal link that serves the ZIP/JS, and to document if it’s possible to automate this.
Content:
Manual:
I’ve already accomplished this, so here’s the snip below showing the default results page. You won’t be able to find this result. Sorry – I ran this scan while I was testing the API, and I wasn’t tracking that it defaults to a private scan. I’ll try to re-accomplish this later in this article.
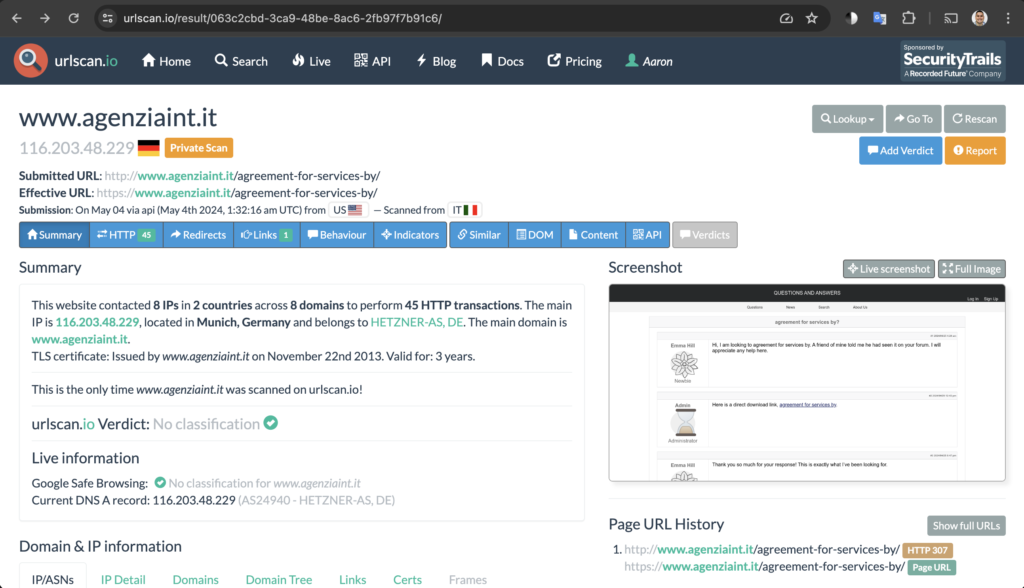
What do we need to check to verify if this is truly a Gootkit lure article? The first indicator is the fake forum that was loaded in the result’s screenshot in the lower right corner of the snip above. Next, Jacob and I previously covered the fake forum loader in “Gootkit is broken right now” (https://malasada.tech/gootkit-is-broken-right-now/#:~:text=The%20fake%20forum%20is%20loaded,and%20finally%207%20hex%20characters). We will be searching for the fake forum loader GET request – the URI (/?af99092=5281112)matches the pattern of /?, 7 hex characters, =, and finally 7 hex characters.
I click into the HTTP transactions tab and scroll for the pattern match. After a quick scroll, I found it under “/”.
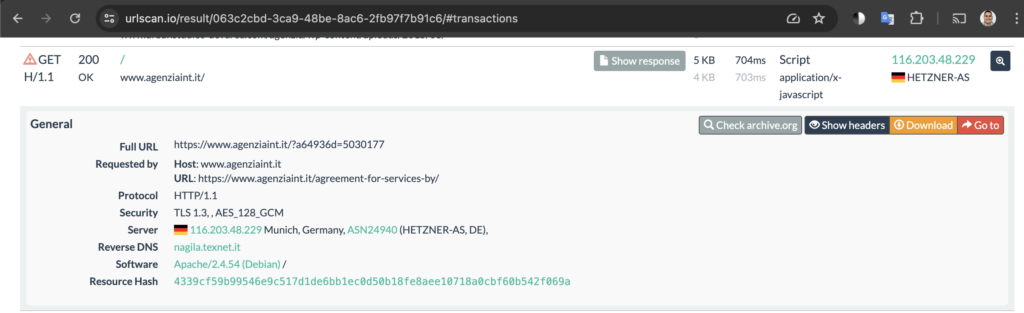
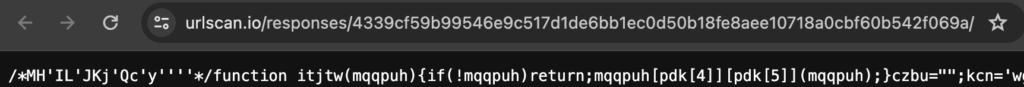
The scan was served the forum loader script, so we can review it by clicking the Show response button. The results are shown below. It’s obfuscated. Check an earlier article if you want a breakdown of this. The main takeaway is that it loads the fake forum.
Next, because the fake forum was successfully loaded, we can see the link info from the fake forum as seen on TV below.
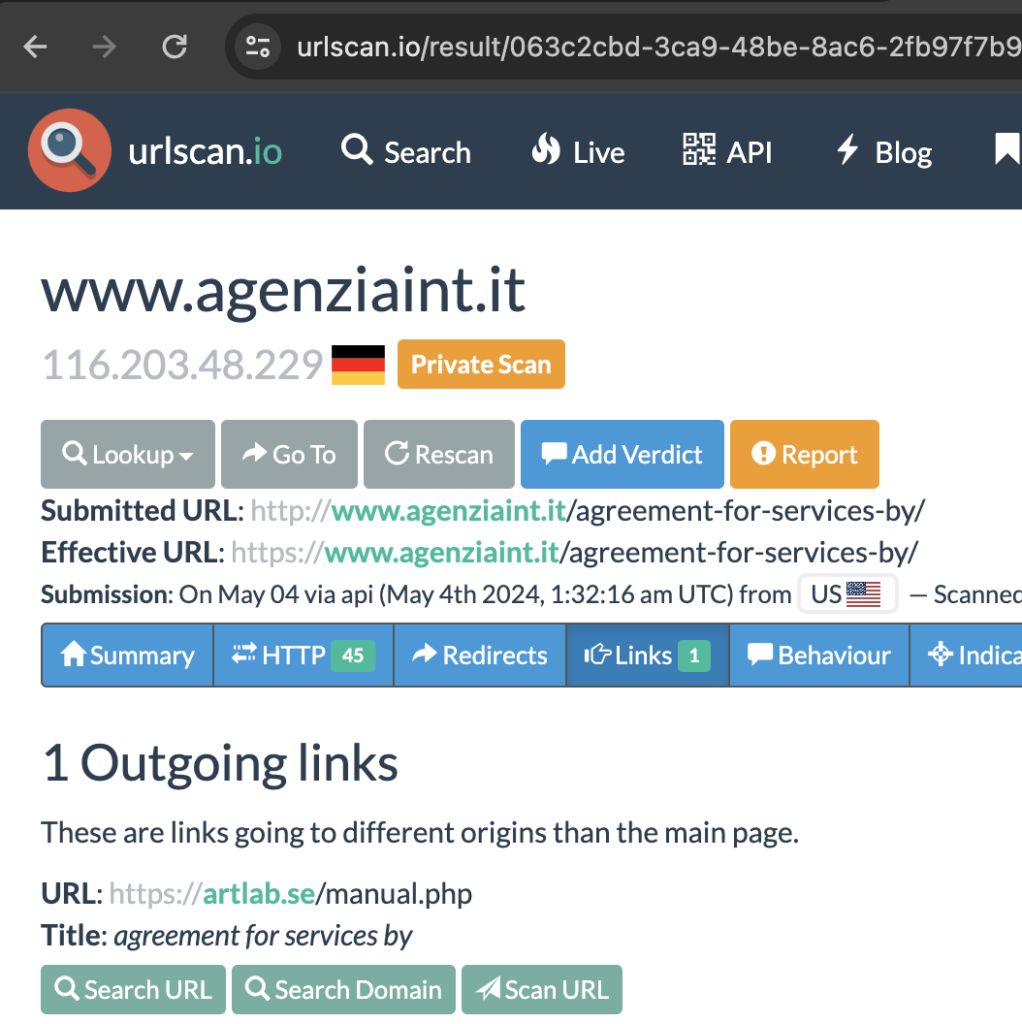
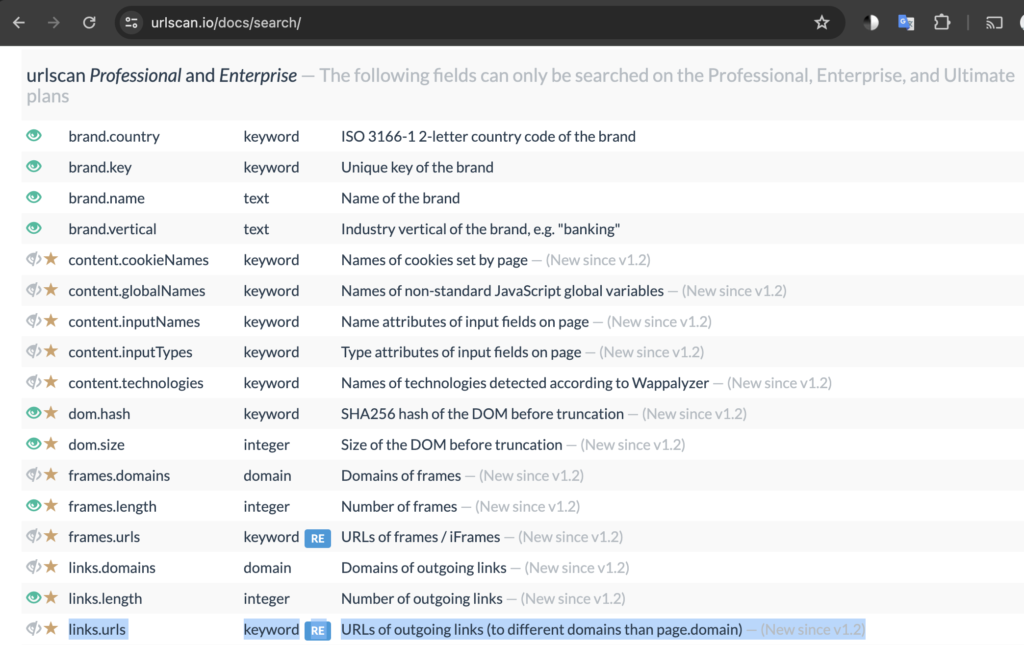
It would be cool if we could search for any other scan results that contained an Outgoing link to the same URL, but unfortunately, it requires a Professional or Enterprise plan.
This is all fantastic, but it would be far out if we could perform the scan and verification process programmatically. The next section will discuss how I accomplished this.
Python:
First, create an account, then get your free API key. Save it to an environment variable, or however you want to store it.
I use Github Copilot to do the “figuring out” for me.
Here’s a snip of the wrapper. It’s fairly simple. The snip below shows the updates I made to set the visibility to public by default, and it also sets the referrer to Google by default (so that it would appear to have originated from a web search).

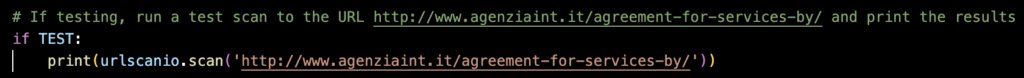
I plan to implement it in loops later, but for now I ran a couple simple tests. First I ran the a quick scan for an article that I already knew is a lure.
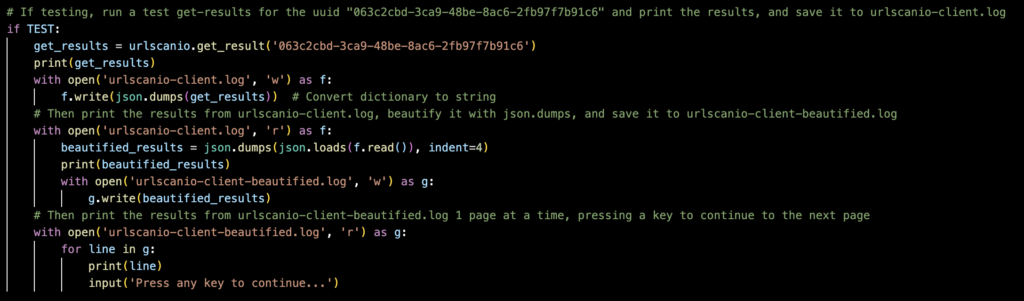
Next, I took the output, and got the UUID (063c2cbd-3ca9-48be-8ac6-2fb97f7b91c6) for the input of the next task. In the snip below, I get the urlscan.io result and store it in get_results. I save the get_results to urlscan-client.log, then I beautify it and save it in a beautified log file for me to read.
I did a quick find in the beautified log to find the fake forum loader call. The key will be “url”. We will need that for the next step.
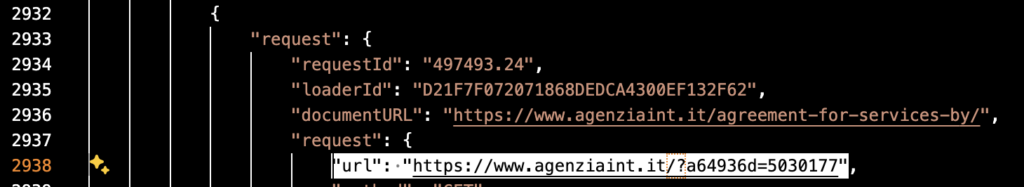
After that, we perform the check for the fake forum loader call. Since we already know it will be the “url” key, I prompted copilot to use that key. Here is the code block below to find it.
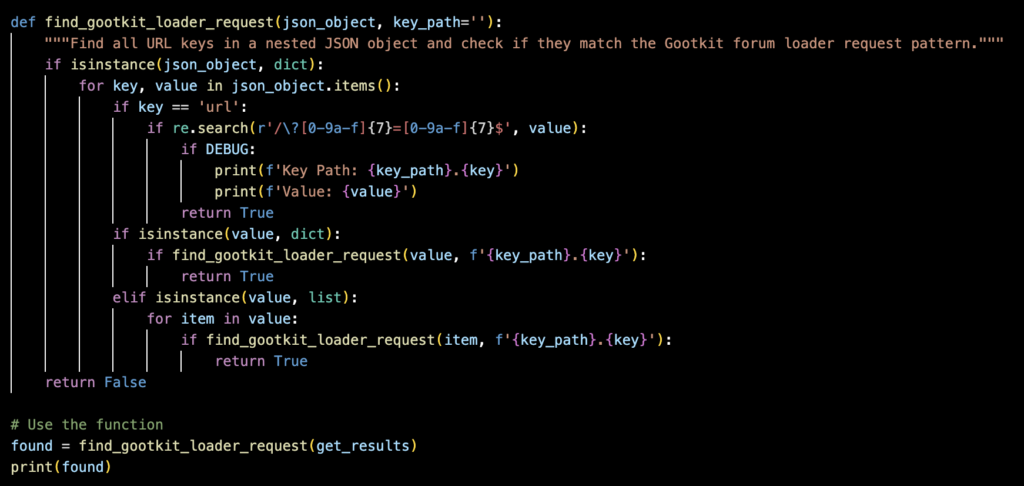
I don’t have the snips, but it returned True.
Additionally, the result object also includes the link to the ZIP/JS server from the fake forum as seen below. It’s pretty cool, and is something I’ll implement in a future iteration.
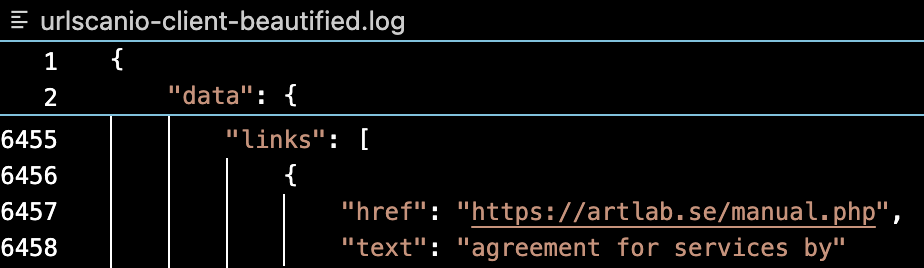
I’ve got a few things I’ll be modifying in the future like separating the scan tasks from the tasks to get the results. I’ll probably take the response from the scan request and save that to a queue file. Then, I’ll have a separate Python that’ll check if there’s anything in the queue, check if it’s been at least 30 seconds since the scan, then get the result and check if it has a fake forum loader call. By separating these tasks, I’ll be able to implement a distributed system where anyone that’s interested can run a specific module. That’s about it for now. Here’s the summary.
Summary:
You can use urlscan.io to check if a URL is a Gootkit lure article. You can do it manually, or you can create some simple Python scripts to perform the tasks for you.
