This documents the analysis I performed on a crypto phishing domain that a phisher DM’d me. It documents how I was able to pivot on file hashes the site served, how I compared domains to observe the pattern, and how I used that pattern to create a Silent Push query to return 120 additional domains.
Table of Contents
Tactical Pause
THE CONTENT, VIEWS, AND OPINIONS EXPRESSED ON THIS DOCUMENT ARE MY OWN AND DO NOT REFLECT THOSE OF MY EMPLOYER OR ANY AFFILIATED ORGANIZATIONS. ALL RESEARCH, ANALYSIS, AND WRITING ARE CONDUCTED ON MY PERSONAL TIME AND USING MY OWN PERSONALLY-ACQUIRED RESOURCES. ANY REFERENCES, TOOLS, OR SOFTWARE MENTIONED HERE ARE LIKEWISE USED INDEPENDENTLY AND ARE NOT ASSOCIATED WITH, ENDORSED, OR FUNDED BY MY EMPLOYER.
The Flow
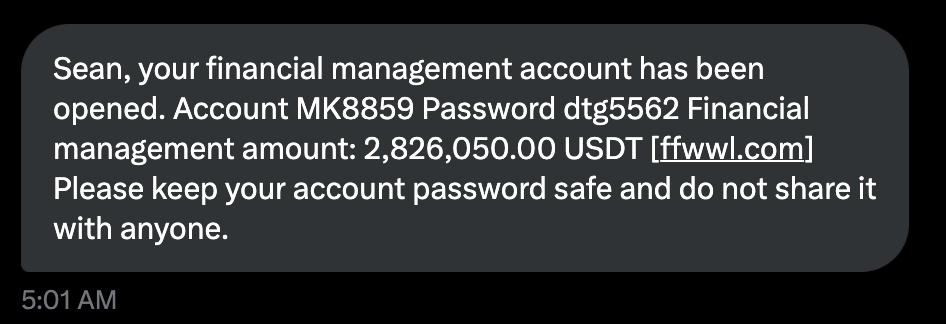
A phisher sent me this DM:

Does anyone fall for these?

I scanned it in urlscan, and I searched on the hash for the “common.js” value. It returns many similar results.

https://urlscan.io/search/#hash%3Ace9f8f9bb4e5eef2462667de0e76e65bd65c6e670cef61b5e76ed47be6813cf9

The additional domains appear to use the same external resource, as seen in the three snips below.



A quick comparison shows they appear to be a campaign activity.

Narrowing down on the shared resource, and searching for that hash returns better results.

https://urlscan.io/search/#hash%3A5f3ec643731be3a71b0845e6d398a07ea21dc3c6d0298150470b3b4a1942cf89

We can generate the nshash to create a query in Silent Push to hunt for more similar domains.

721b081047884780535c262ccfae8ed5
Ran a WHOIS query in Silent Push:

Spot check one result with 0 scans:

This appears to use a different template, but it’s still a crypto-themed lure.
https://urlscan.io/result/01960cf5-31c4-75fd-b294-0fb9d7109ac8

Success!
I check two more from this search:
https://urlscan.io/search/#hash%3A5f3ec643731be3a71b0845e6d398a07ea21dc3c6d0298150470b3b4a1942cf89


They have the same NSHASH, and a different registrar and creation dates from the last comparison, but this pair has the same creation date/time.
This query isn’t too great:

I removed the created filter and got better results. It looks like there are many within the same minute.


I removed the create time filter on the first WHOIS scan job and got better results.

I picked a random value to sample:

Success:
https://urlscan.io/result/7c0196a8-118e-4979-ac6c-6510b6c731f3

Awesome!
Update 20250413: Domain Length
I’m adding this section for a reference to the Defender’s ThreatMesh Framework (https://github.com/MalasadaTech/defenders-threatmesh-framework). Given the domains follow the pattern of five random letters followed by the .com TLD, we can create a pivot on that. This pivot will be in used in addition to the nshash and registrar. In Silent Push, we can implement this with “domain LIKE ^[a-z]{5}\.com$”. The snip below shows the implementation along with the head of the results.

Summary
I received a crypto phishing DM. I analyzed the domain, pivoted off website hash values and found additional domains. I compared those additional domains to determine the patterns. I used those patterns to run a Silent Push query that returned 121 unique domains from this campaign.
IOCs
aiqde[.]com
aojcs[.]com
axwvu[.]com
bbxgg[.]com
bfcrr[.]com
bfrdm[.]com
bgyor[.]com
bitbmq[.]com
bitdxg[.]com
bitfcv[.]com
bitgvy[.]com
bithfb[.]com
bithva[.]com
bitifw[.]com
bitlkl[.]com
bitmfi[.]com
bitopa[.]com
bitwwk[.]com
bitxae[.]com
bitxji[.]com
bitxxi[.]com
bitznm[.]com
bitzsx[.]com
ckwcb[.]com
cnhxbh[.]com
ctyvn[.]com
cuofk[.]com
cycaz[.]com
dwbge[.]com
dxzzr[.]com
dyxqq[.]com
eeblb[.]com
eeqii[.]com
ehruk[.]com
ekuez[.]com
envpz[.]com
etusv[.]com
frnxc[.]com
ftoue[.]com
fxeou[.]com
gczbc[.]com
gmnyy[.]com
gtkcm[.]com
hteht[.]com
icxdu[.]com
idzrg[.]com
imvcd[.]com
jccxz[.]com
jmkrw[.]com
jonbg[.]com
jwuqp[.]com
kekth[.]com
kghzt[.]com
knbrq[.]com
kzfvv[.]com
lcxff[.]com
lczzt[.]com
lktfc[.]com
lkyyn[.]com
mwevp[.]com
nbulo[.]com
nmnox[.]com
nolvb[.]com
npdzc[.]com
nppec[.]com
nrkav[.]com
nrrww[.]com
ntehb[.]com
ntkwc[.]com
ntuop[.]com
numxd[.]com
nxkpg[.]com
oobvf[.]com
oxlop[.]com
ozwzy[.]com
pgcuu[.]com
ppegm[.]com
pukae[.]com
qiwmm[.]com
qlcoo[.]com
rjseh[.]com
rseph[.]com
rtrfr[.]com
rtwub[.]com
rvuca[.]com
rwvdq[.]com
sicug[.]com
slmbb[.]com
tiezc[.]com
tyyse[.]com
uofrf[.]com
upepk[.]com
uygou[.]com
vaiuv[.]com
velvg[.]com
vkkbr[.]com
vmvxw[.]com
vtieq[.]com
vysxx[.]com
vyypd[.]com
wbhaa[.]com
wfwfk[.]com
wfzxt[.]com
wiccg[.]com
wmdgg[.]com
xascr[.]com
xngzc[.]com
xrvbc[.]com
xstbr[.]com
xtiwq[.]com
xtytp[.]com
xvobn[.]com
xwbiu[.]com
ykwxh[.]com
ynpdd[.]com
ytwdd[.]com
yzkac[.]com
zckno[.]com
zeolm[.]com
zlnpa[.]com
znzgw[.]com