Table of Contents
TL;DR
This documents my research into three methods an attacker could use, with an SVG file, in a phishing attack to direct the victim to the next stage in the delivery. This analyzes how each method differs. The recommendations includes steps for everyone (courtesy of the FBI Denver Field Office), and it also includes steps SOC Analysts could take to hunt for suspicious behaviors within their network.
Tactical Pause
THE CONTENT, VIEWS, AND OPINIONS EXPRESSED ON THIS DOCUMENT ARE MY OWN AND DO NOT REFLECT THOSE OF MY EMPLOYER OR ANY AFFILIATED ORGANIZATIONS. ALL RESEARCH, ANALYSIS, AND WRITING ARE CONDUCTED ON MY PERSONAL TIME AND USING MY OWN PERSONALLY-ACQUIRED RESOURCES. ANY REFERENCES, TOOLS, OR SOFTWARE MENTIONED HERE ARE LIKEWISE USED INDEPENDENTLY AND ARE NOT ASSOCIATED WITH, ENDORSED, OR FUNDED BY MY EMPLOYER.
Background
I recently posted about an interesting Any Run sample I came across on X (https://x.com/MalasadaTech/status/1900810121988735315). I thought it was interesting because this was my first time seeing an SVG with ECMAScript in it (although the capability has been around for a while). This piqued my interest. This post might be a bit more “bloggy”.
The Any Run session (https://app.any.run/tasks/6dfa0a86-56c0-49e3-8a02-67320f271a28) shows the flow below:
ACH Incoming 031425 Remittance_PayeeRemittanceNotice_6a1f51f006fa3bd9268d6f96e5695f91.msg >> 25 Remittance_PayeeRemittanceNotice_6a1f51f006fa3bd9268d6f96e5695f91.msg (attached) >> ACHStub_XNZSCHPTIF.svg (attached).
ACHStub_XNZSCHPTIF.svg had ECMAScript within it that was used to forward the location to the next stage on irtickli[.]com without a click. I’ve previously observed many Any Run sessions that used an SVG attached in a double-attached email, but they required the user to click the SVG image. Unfortunately, the Any Run session didn’t have the network traffic that led to the initial irtickli[.]com domain. I really needed the network artifacts so that I could learn the behavior pattern that can be hunted on.
Question: Will the GET request for the next stage include the Referer field (that is for the clickable kind, and the one that doesn’t need a click)?
Directing the victim from the SVG to the next stage
There are three ways to accomplish this. The first way is by using the SVG to set the window.location.href to the next stage, another method is to use the SVG to set the window.parent.location.href to the next stage, and another way is to turn the SVG into a clickable link by creating an anchor and setting its xlink:href attribute. Each method will have different requirements.
I was having issues with Any Run, so I had to test the parts below using Burp. The snip below shows the initial request for RenderSVG.html. It is a simple HTML file that loads testAlertES.svg as an img, and it loads testAlertESObj.svg as an object.

The snip below shows the request/response for testAlertES.svg. When using the window.location.href value, it will not forward the victim to the next stage if it is added to the page with img. Also, the alert doesn’t work. Note how the request includes the Referer value that is set to the referring URL.

The snip below shows the request/response for testAlertESObj.svg. When the SVG is rendered as an object, and it has window.parent.location.href, it succeeds in forwarding the victim to the next stage as seen in the next snip.

The snip below shows the request/response for sama.la. It shows the Referer field is set, and it was referred by testAlertESObj.svg. In this scenario, I would expect the phisher to double attach an email with an HTML file that loaded an attacker-controlled SVG file to set the window.parent.location.href value.

The snip below shows the request/response for testAlertES.svg from when I tried to access the SVG file directly. It succeeded in forwarding me to sama.la, but for some reason Burp wasn’t capturing the next request to sama.la.

I had to use Any Run to test this. Here is the session link: https://app.any.run/tasks/1cd081e3-3d1c-4c83-a6a9-cbc1115c28db
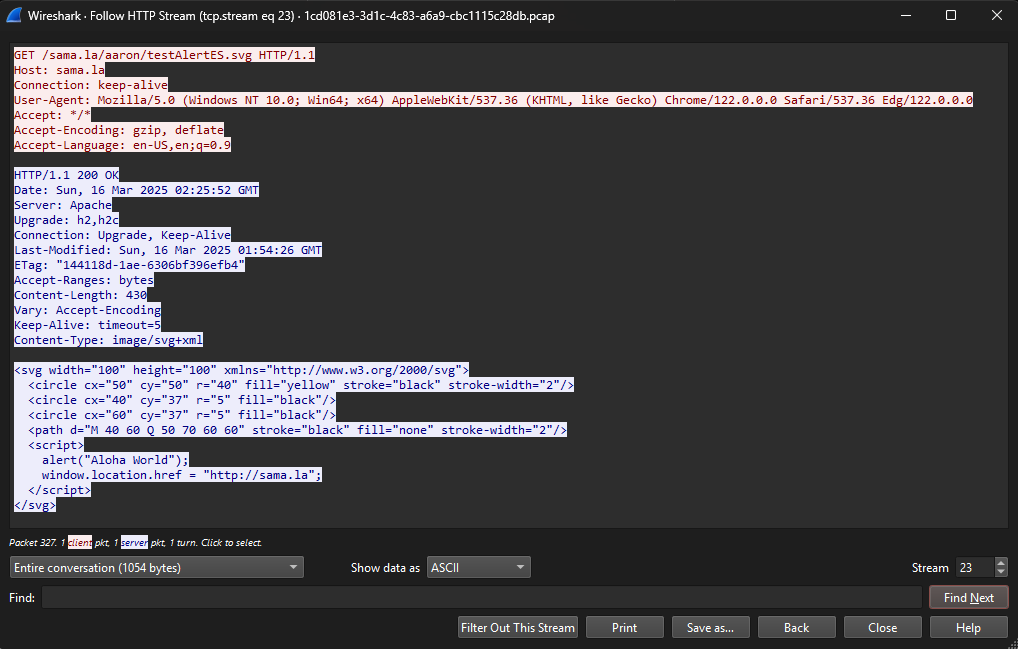
The Wireshark snip below shows the request/response for the testAlertES.svg file that sets the window.location.href value.

That succeeded in forwarding me to the next stage, but the GET request for the next stage did not include the Referer value. The snip below shows the request for the next stage (sama.la).

I wanted to check if this would be the same if it was an HTML file that directed the victim to the next stage by setting the window.location.href. Here’s the Any Run session: https://app.any.run/tasks/9996270a-d94c-4036-a766-a691e870fe67
The Wireshark snip below shows the request/response for window-location-href.html that uses window.location.href, and it shows the GET request for the next stage that does not include the Referer field. We can deduce this is normal behavior that is not specific to the SVG.

SVG xlink:href value
The last method to try is to make the SVG a clickable link. Here’s the Any Run session: https://app.any.run/tasks/10daa259-2593-47b4-8fb3-1d9c520bed96
The Wireshark snip below shows the request/response for the testahref.svg file with the xlink:href value set to the next stage.

The Wireshark snip below shows the GET request for the next stage (sama.la), and it shows the Referer field set to testahref.svg.

Conclusions
The Referer field is set in the next request when the SVG is loaded on an HTML file as an object with the window.parent.location.href value set. This method will redirect the victim to the next stage without any other steps. In the context of a phishing email, the attacker only needs to trick the victim into opening the HTML file for this part of the delivery.
The Referer field is also set in the next request when the SVG is configured as a clickable link by setting the anchor xlink:href value. In the context of a phishing email, the attacker will need to trick the victim into opening the SVG, and then the attacker will also need to trick the victim into clicking the SVG for this part of the delivery.
The Referer field is not set when the SVG is accessed directly, via a web browser (…forgot to mention that part earlier… it is assumed), and the SVG window.location.href value is set. In the context of a phishing email, the attacker would only need to trick the victim into opening the SVG file for this part of the delivery.
Recommendations
“Take a breath, slow down and think. Be aware of your actions online and what risks you could be exposed to.” – FBI Denver Field Office (https://www.fbi.gov/contact-us/field-offices/denver/news/fbi-denver-warns-of-online-file-converter-scam)
- Search network traffic logs for suspicious requests that include an SVG file as the Referer
- Search network file logs for suspicious SVG files that include script tags, or xlink:href values
- Search network traffic logs for suspicious GET requests for SVG files that do not include the Referer field, because this may indicate the SVG file was accessed via the email desktop application.
Summary
This documents my research into three methods an attacker could use, with an SVG file, in a phishing attack to direct the victim to the next stage in the delivery. This analyzes how each method differs. The recommendations includes steps for everyone (courtesy of the FBI Denver Field Office), and it also includes steps SOC Analysts could take to hunt for suspicious behaviors within their network.