Table of Contents
Using Silent Push to find the following infrastructure
- SmartApeSG (Tracked as ZPHP by @Proofpoint)
- LandUpdate808 (Also tracked as Kongtuke by @monitorsg)
- TA582
TL;DR
You can use Silent Push’s query builder to monitor certain adversary infrastructure based on simple properties such as ASN, name server, registrar, and domain pattern.
This will extend my previous post here:
Tactical Pause
THE CONTENT, VIEWS, AND OPINIONS EXPRESSED ON THIS DOCUMENT ARE MY OWN AND DO NOT REFLECT THOSE OF MY EMPLOYER OR ANY AFFILIATED ORGANIZATIONS. ALL RESEARCH, ANALYSIS, AND WRITING ARE CONDUCTED ON MY PERSONAL TIME AND USING MY OWN PERSONALLY-ACQUIRED RESOURCES. ANY REFERENCES, TOOLS, OR SOFTWARE MENTIONED HERE ARE LIKEWISE USED INDEPENDENTLY AND ARE NOT ASSOCIATED WITH, ENDORSED, OR FUNDED BY MY EMPLOYER.
Previous work
Previously, I documented how to track SmartApeSG/ZPHP infrastructure using the Silent Push Web Scanner search results (https://malasada.tech/using-silent-push-to-detect-smartapesg-iofas/).
Brief summary on that: SmartApeSG/ZPHP domains use a particular template, and you can find other SmartApeSG/ZPHP domains by searching for the template on the given AS.
I’ve also been using this technique to track LandUpdate808/Kongtuke (https://infosec.exchange/@MalasadaTech/113352445891544246).
LIMFAC
One limiting factor with this technique is that a web scan task must be initiated. It would be great if there was a way to find infrastructure absent of web scan tasks.
Possible Solution
Chris Duggan (@TLP_R3D) shared a technique using DNS Coffee to track ScatteredSpider infrastructure (https://x.com/TLP_R3D/status/1845446668549775372)
I was able to recreate that DNS Coffee workflow to track TA582 infrastructure (https://infosec.exchange/@MalasadaTech/113499380416461684).
Using Silent Push
I’m pretty stoked to find that this can be accomplished using Silent Push.
The snip below shows how to navigate to the search page, the search values (for SmartApeSG/ZPHP), and the results box.
To navigate to the search page: Advanced Query Builder >> Domain Queries >> search

SmartApeSG/ZPHP
As seen in the snip above, the SmartApeSG/ZPHP values are:
nsname = dns1.regway[.]com
asnum = 202015
Here’s the table view:

For LandUpdate808/Kongtuke
There are a few caveats for this one. There were a bit too many unrelated domains, so I had to add the registrar value. Also, the search takes longer than the timeout, so you can see the result status shows “STARTED”. You’ll have to give it about 3 MISSISSIPPI’s before you blitz and click the retry JobID button.
nsname = *.ns.cloudflare[.]com
asnum = 399629
registrar = Global Domain Group LLC

I clicked the button to explore in table view, and then exported to CSV. There are some WP Engine domain variations (They don’t appear to be LU808/Kongtuke – no other comment on those at this time). Aside from those WP Engine variation domains, the rest of the domains appear to be strictly LandUpdate808/Kongtuke.
20250701 UPDATE!
I’ve become aware of CyberCX’s research on what their calling DarkEngine (LandUpdate808) here: https://connect.cybercx.com.au/dark-engine. In their research, they’ve found that the WP Engine masquerade domains were used for phishing. Check out their work for more info.

TA582
LandUpdate808/Kongtuke currently uses TA582 infrastructure. I don’t have too much info on TA582 infrastructure other than the observation that the URI path “{TA582 Domain}/1.php?s=527” is used for this, and it should forward you to Google when you try to access the domain. (Side note, there’s another campaign that is using the “/1.php?s=mints13” URI path.). You can track the TA582 infrastructure using the values below.
nsname = ns1.he[.]net
domain_regex = ^.*\.top$
asnum = 399629

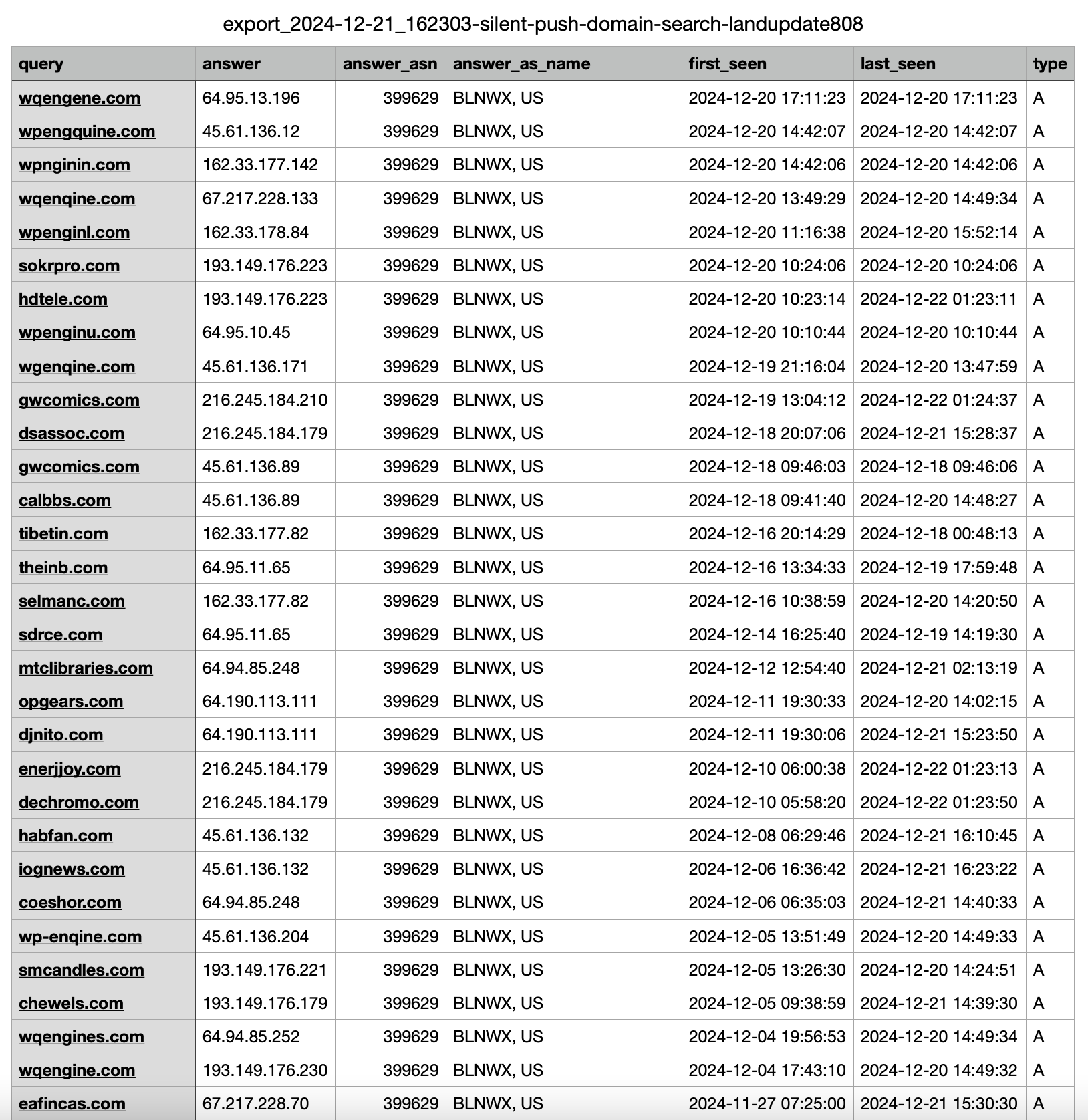
Here’s a snip of the CSV, sorted descending by first_seen (pulled on 21DEC24).

Constraints
There are some infrastructure that isn’t unique enough to identify via basic properties. Some use VERY common name servers and Autonomous Systems. These would need a workflow that could be found by combining DNS searches and web scans to non-standard URI paths (“{Domain}/api” for Lumma Stealer, for example) for validation. I will be working on something in the near future that may combine the two.
[…] LandUpdate808 Analysis ClickFix Delivery Initiated via Phishing Email Silent Push to find SmartApeSG, LandUpdate808, and TA582 Infra Lumma Stealer Delivered via YouTube Videos for Cheats ClickFix Baddys via RussianPanda’s […]