Table of Contents
Intro
@Gootloader recently published a new article showing how he found the Gootloader TA has updated their delivery vector. Previously, Gootloader was delivered by tricking the victim into thinking the malware was an answer to a question they were searching for. Now, it is delivered via an online PDF tools site. This document will discuss methods that I used to find Gootloader fake forum articles. While it no longer applies to Gootloader, it could be helpful for researchers in other endeavors.
Before I continue, I think it may be beneficial to specify the different “Gootloader” references. My reference to Gootloader is a reference to the malware that’s delivered, but it could also reference the Gootloader operators, or Gootloader threat actors. @Gootloader is the researcher that tracks and shares info about the Gootloader TA (his blog: https://gootloader.zip).
THE CONTENT, VIEWS, AND OPINIONS EXPRESSED ON THIS DOCUMENT ARE MY OWN AND DO NOT REFLECT THOSE OF MY EMPLOYER OR ANY AFFILIATED ORGANIZATIONS. ALL RESEARCH, ANALYSIS, AND WRITING ARE CONDUCTED ON MY PERSONAL TIME AND USING MY OWN PERSONALLY-ACQUIRED RESOURCES. ANY REFERENCES, TOOLS, OR SOFTWARE MENTIONED HERE ARE LIKEWISE USED INDEPENDENTLY AND ARE NOT ASSOCIATED WITH, ENDORSED, OR FUNDED BY MY EMPLOYER.
Summary Up Front
We will discuss how Gootloader lure articles are boosted in the search engine result because of backlinks. We will discuss how you can crawl the old Gootloader sites by crawling the backlinks to find the lure articles, and you can crawl the Gootloader sites to find all the lure articles hosted on a single site. It’s easiest to crawl a site by incrementing or decrementing the short link. We will discuss how @Gootloader found the new Gootloader delivery vector using online PDF conversion sites. We will discuss how you can find other templates for testing by searching Silent Push for the HTML title. The next steps will be to keep testing and trying to get the online PDF sites to serve Gootloader. Also, it will be important to monitor for any updates from the greater community.
Primer
This will focus on the delivery TTPs. It will not go into the payload or beaconing. This assumes you already have a working knowledge of the Gootloader fake forum. If you don’t – here’s the basics. A user would search for something in a search engine, and they’d get served a link to a fake article on a Gootloader compromised site. The lure would present a fake article that appeared to be an AI generated article that discusses the search query. If the visitor met the requirements to be served Gootloader, the site would serve a fake forum with a link to download the malicious JS file in a ZIP. The image below shows an example of what the fake forum looks like. The search term the visitor would’ve been searching for is “microsoft enterprise purchase agreement”.

SEO Poisoning
How was the Gootloader TA able to get their lure articles high in the search ranking? They achieved that via SEO Poisoning. I’ve had an issue with this. Early into first learning about Gootloader, I read many reports saying they used SEO poisoning. Folks in my proximity agreed, but when I asked for clarification no one could explain how the SEO poisoning was accomplished. I found, and I like, the Crowdstrike definition of Blackhat SEO. The snip below shows the pertinent part.

Image retrieved from Crowdstrike here: https://www.crowdstrike.com/en-us/cybersecurity-101/social-engineering/seo-poisoning/?srsltid=AfmBOorsr6STeUxADgnDLNNyu8DMl0DDDXdOtOHI9rBdQsXEkhA3PJJY#:~:text=Example%20of%20seo%20poisoning%20on%20a%20search%20engine%20result
I’ve observed the Gootloader TA use cloaking and private link networks tactics for SEO poisoning. They don’t appear to use keyword stuffing, because the words are related to the lure article topic. For manipulating search ranking, I don’t know how an outside researcher could determine if bots or humans generated fake clicks. I imagine employees at a search engine company could determine this, but not me. Let’s get into cloaking and using private link networks.
Cloaking
The main page of the Gootloader sites have a list that is not displayed to regular users. It is hidden via the div style “display: none;”. In the snip below, you can see how the “display: none;” style property is applied, and you can see the list items for the lure articles.

When I delete the style property, we can see the list on the compromised site – as seen in the snip below.

When I view the page source, I’m presented with the div without the style to hide it. You can see this on line 467 in the snip below. Also, you can see the first list item. It is not beautified when you view the page source, so you can only see the first list item, but you get the idea.

Private Link Networks (Backlinks)
This is where the fun starts. For each Gootloader-compromised site (or domain), you can find many of the backlinks. First, you need to find a compromised domain, and then search for backlinks. I use the backlinks checker from ahrefs (here: https://ahrefs.com/backlink-checker). It is free, although it’s limited – it’s good enough.
I start by putting in the compromised site and I search on subdomains.

The snip below shows the top of the result.

We can see that it has a very low domain rating. I found many articles state that blackhat SEO techniques only boost the ratings temporarily. They say that the search engines will eventually detect it, and penalize the domains with lower ratings. I assess that the backlinks for this domain have been detected, and the domain rating has been decreased because of it.
The first result is not a Gootloader backlink farm. It is a spam message for the compromised site owner to see. When (or IF) the site owner checks their backlinks, they will see this SEO booster’s message for them. It is advertising that they can boost the domain rating.
The next results are the backlinks we’re looking for. The snip below shows them better.

The links on the left are the backlink articles, and the parts on the right show the links and the anchor text as it is in the paragraph. We will go to the first backlink article: hxxp[:]//greentertainment[.]com/agreements-and-contracts-ensuring-compliance-and-clarity/. I’ve ran a scan task in urlscan for your viewing pleasure. You can access it here: https://urlscan.io/result/542e4251-0101-4599-8ce6-7c344f746d29/#summary. The snip below is the page snip from the urlscan task.

You can see it contains unrelated paragraphs that hit the “agreement”/”contract”/”legal” keyword theme. You can view the urlscan links section to find this Gootloader lure URLs here: https://urlscan.io/result/542e4251-0101-4599-8ce6-7c344f746d29/#links. The snip below shows the outgoing links.

I scanned the first URL. You can see the results here: https://urlscan.io/result/350eb2f6-64f0-4a7e-a22a-922c1d564407/. Here is a snip of the page from the urlscan result below.

This is the lure article that gets overwritten with the fake forum.
How do we know this is a Gootloader fake forum?
Sophos shows us the lure article has a very unique script call here: https://news.sophos.com/en-us/2021/03/01/gootloader-expands-its-payload-delivery-options/#:~:text=The%20modified%20code%20is%20a%20simple%20script%20tag%20that%20looks%20like%20this%3A. The snip below is from the Sophos article, and it shows the unique script call.

The unique script call contains a seven character hex for the site ID, and a seven character hex for the article ID as the key-value pair. We can confirm this article is indeed a Gootloader lure by viewing the DOM here: https://urlscan.io/result/350eb2f6-64f0-4a7e-a22a-922c1d564407/dom/. The snip below shows a script call with a similar pattern.

What’s the benefit?
We’ve got the backlink article, and we’ve got the method to validate that it’s a Gootloader lure article. What’s the benefit, and what can we do with this? With this, we should be able to follow the flowchart below for an infinite IOC life-hack.

This could be a bit inefficient. It would be better to crawl each backlink site to capture ALL of the Gootloader backlink articles. Additionally, we should do the same for the Gootloader articles.
Crawling Using the Shortlink
I tried a few methods to crawl the backlinks. I first tried to use the sitemap, but that didn’t go too well. I found that the backlink sites didn’t all use the same SEO plugin, so the sitemaps were different. I found that all of the backlink sites used WordPress. I found that WordPress uses short links. The URLs that we are used to are the canonical links. There are numbered links that we can use for crawling – these links are called shortlinks. In the urlscan task DOM, here https://urlscan.io/result/350eb2f6-64f0-4a7e-a22a-922c1d564407/dom/, we can see the canonical and shortlink as seen below:

We benefit from this because we can crawl the site by incrementing and decrementing the shortlink number by one (sometimes they go by two for some reason). I’ve incremented the shortlink number by one, and I’ve ran the urlscan job here: https://urlscan.io/result/420f1541-cc53-4783-9967-8e9c4b285e99/. You can view that it is a new Gootloader lure article in the snip below.

Given this process, you can now crawl each Gootloader-compromised site to find all of the Gootloader lure articles. Similarly, you can repeat the process for the backlink articles. Crawling the backlink articles are a bit more tricky. Backlink sites don’t only boost Gootloader lures. I’ve observed they also boost a lot of online casinos and online dating sites. They also boost the occasional layman trying to boost their site (sadly). The online casinos and online dating sites are simple to filter out. They will only link to one online casino or dating site per article. The Gootloader site will have at least 9 paragraphs, and all of the paragraphs will be a child to a single div. This is unique to the Gootloader boosted backlinks. I was able to accomplish this with the code in the snip below. It’s a snip from my Gootloader crawler project.

Now, your super-duper kewl flow chart should look something like this:

Happy crawling! ALSO – of course, there’s an implied “check robots.txt to see if crawling is not allowed”…
Backlink easy button?
You may be wondering if there’s a backlink easy button. Is there a way we can get a starter list of backlinks? Yes! Yes there is! I’ve reviewed 3.41 bajillion backlink article titles, and I’ve observed a pattern that can be used to find them. I’ve observed that some of them have “unique title:” in the article title. I suspect they used some kind of automation to create all of the backlink article titles, and somewhere down the line it messed up. Perhaps it was an AI prompt that went unverified. In any case, we can dork it up. If you dork just on that, it will return too many unrelated articles. If you scope it down to only include results that have the Gootloader keywords agreement, contract, and legal, then it should be good. See the polished Google dork below.
intitle:”Unique title” intext:”agreement” intext:”contract” intext:”legal”
Here’s a snip of the results.

Some sites will be down by the time you view them. For example, that Ghana government link in the snip above no longer works. I’m assuming they found it was not official content and they’ve removed it.
What Happened?
At some point, I noticed I wasn’t able to download Gootloader any more. With all of the great research that @Gootloader was posting about the Gootloader C2, I thought maybe the TA had finally found a way to block researchers. While I was researching, I found an article by the Internet Janitor.
The Internet Janitor
I don’t have the original URL that I found, but here’s an example article by the Internet Janitor: https://idee.education/en/2022/02/27/gootloader-infection-cleaned-up/. See the snip below for the top of the article.

In the article that I first found it on, it was listed on the main page where they had a list of most recent articles written. Since finding these articles, I’ve put Gootloader research on hold while I monitored for updated research from others.
The New Stuff!
The gist of the new delivery process is that the Gootloader is being delivered via online PDF conversion sites. The victim uploads a document they need to process, and if they meet the requirements, they’re served Gootloader. The first domain @Gootloader lists is pdf-online-tools[.]com. Based on my current understanding, there is no determination on if the TA is operating these PDF converter sites, or if the PDF converter sites are compromised. In any case, can we find similar domains? YES!
It’s a Template
The pdf-online-tools site uses a PDF Tools template by “Dosana”. I found this because I was reviewing a scan result, here: https://urlscan.io/result/db82a823-7fc8-4ff5-a659-105f2d844559/, and I searched the page image with Google Lens and observed the Youtube video here: https://youtu.be/faOt6aDZJBM?si=tBddD5QsmDV97SC6.

In the video, “Dosana Dev” runs through the steps of setting up your own site from the template. Interestingly, the video shows that the Namecheap user “dosanaweb” has the domain pdf-online-tools[.]com registered, and it is applied to the web app in the video. This is interesting to me. At first I was wondering if Dosana was involved with the gig, but I am thinking they just made the template and their site may be compromised. In any case, we should check if we can find any more PDF Tool sites.
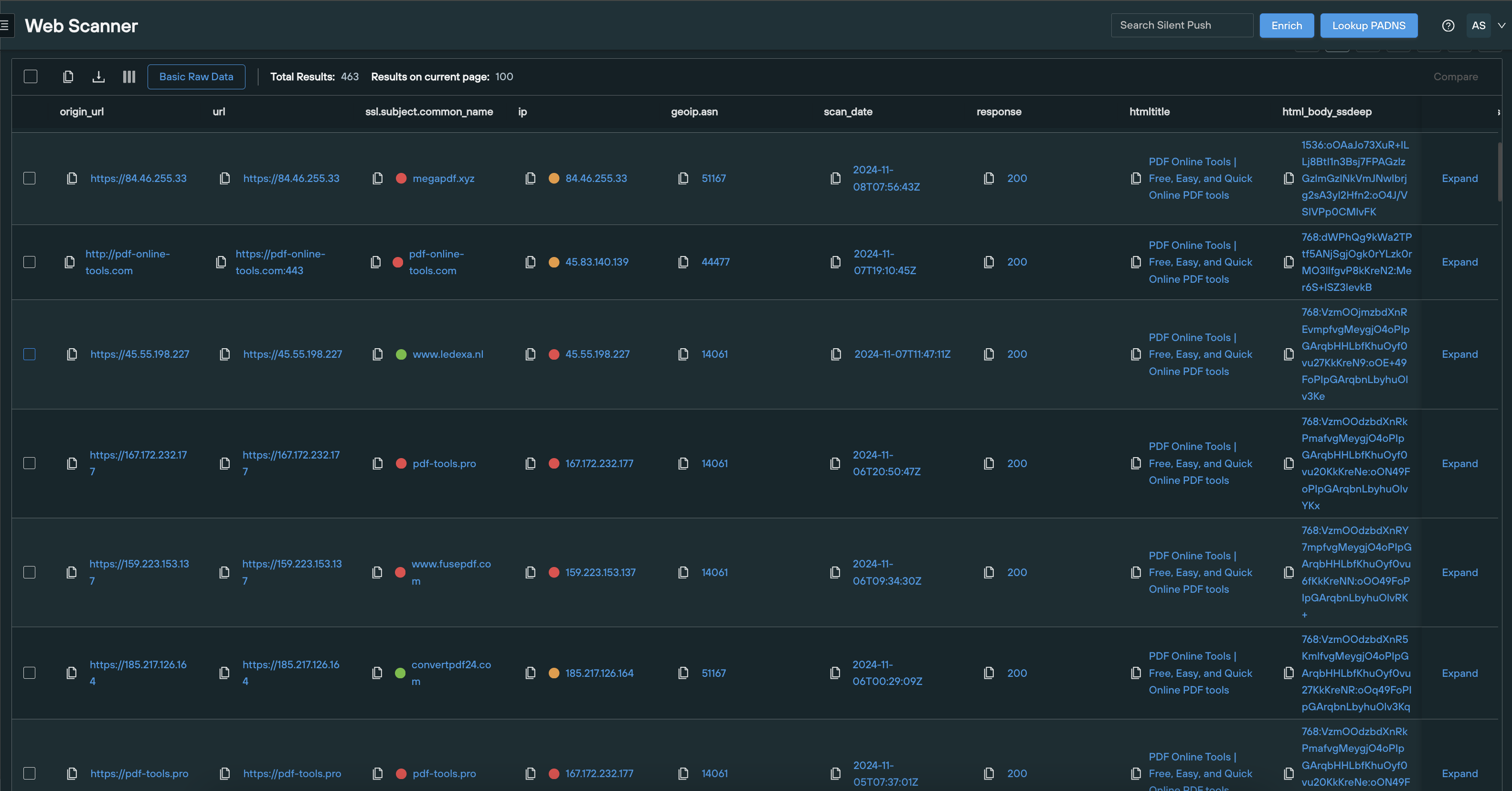
Finding More with Silent Push
Since this is a template, we should be able to find similar domains based on simple things like the favicon or title. From this urlscan task here https://urlscan.io/result/9978468c-d837-4829-b7fb-fdd1112c3789/, we can copy the title “PDF Online Tools | Free, Easy, and Quick Online PDF tools”. With that, you can run this simple Silent Push query:
htmltitle = “PDF Online Tools | Free, Easy, and Quick Online PDF tools”
The snip below shows some domains that could be tested (search results from 08 NOV 24).

I haven’t been able to get it to serve me Gootloader yet, so this is just about the end of the line for now. I’ll be circling back to these domains periodically to see if I can get it to serve Gootloader.
Summary
We discussed how Gootloader lure articles are boosted in the search engine result because of backlinks. We discussed how you can crawl the old Gootloader sites by crawling the backlinks to find the lure articles, and you can crawl the Gootloader sites to find all the lure articles hosted on a single site. It’s easiest to crawl a site by incrementing or decrementing the short link. We discussed how @Gootloader found the new Gootloader delivery vector using online PDF conversion sites. We discussed how you can find other templates for testing by searching Silent Push for the HTML title. The next steps are to keep testing and trying to get the online PDF sites to serve Gootloader to me. Also, it will be important to monitor for any updates from the greater community.
MAHALOZ AND ALOHAZ!
IOCs
I am not listing IOCs because I am not adding anything that hasn’t already been reported. Also, the domains that are listed in the Silent Push snip are not confirmed to serve Gootloader. They are just domains that use the same PDF Tools template. When I do confirm a PDF Tools site is serving Gootloader, I will post about it separately.