I’m a big fan of monitoring FakeUpdate stuff. It appears that TA569 may be increasing their infrastructure, as there was additional TA569 middleware infra observed.
THE CONTENT, VIEWS, AND OPINIONS EXPRESSED ON THIS DOCUMENT ARE MY OWN AND DO NOT REFLECT THOSE OF MY EMPLOYER OR ANY AFFILIATED ORGANIZATIONS. ALL RESEARCH, ANALYSIS, AND WRITING ARE CONDUCTED ON MY PERSONAL TIME AND USING MY OWN PERSONALLY-ACQUIRED RESOURCES. ANY REFERENCES, TOOLS, OR SOFTWARE MENTIONED HERE ARE LIKEWISE USED INDEPENDENTLY AND ARE NOT ASSOCIATED WITH, ENDORSED, OR FUNDED BY MY EMPLOYER.
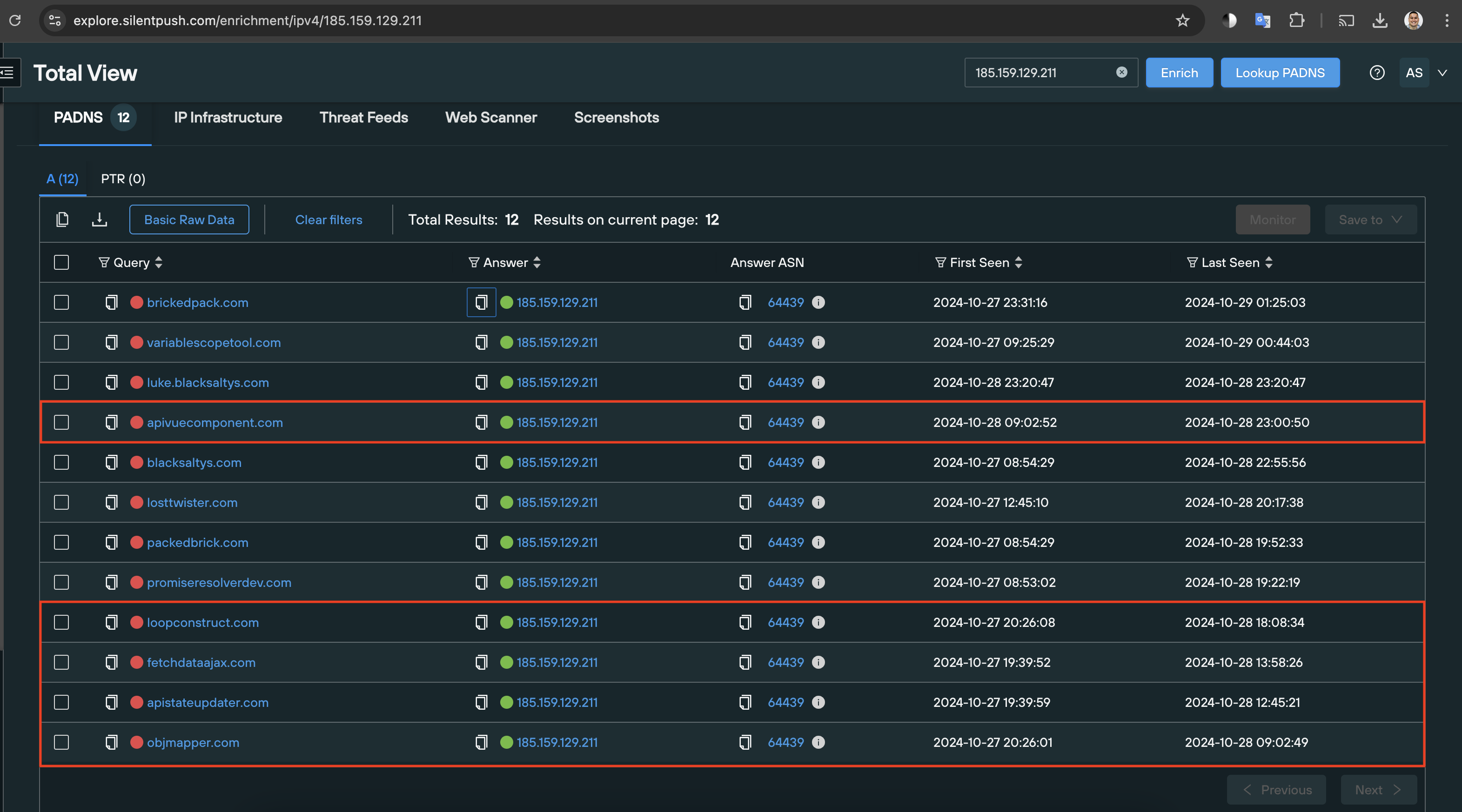
On 27OCT24 I observed there were two new domains associated with TA569 – as seen in the red box in the snip below.

Randy previously reported the first four on 11AUG24 in his “Toot” here: https://infosec.exchange/@rmceoin/112945569100310376 in a reply to Monitor SG.

On 28OCT24, Proofpoint added promiseresolverdev[.]com to their Emerging Threats rules as seen here https://community.emergingthreats.net/t/ruleset-update-summary-2024-10-28-v10729/2083 and in the snip below.

I checked today, and there are more domains that aren’t reported (in addition to variablescopetool[.]com).

I checked for scan tasks in urlscan, submissions in Any Run, I checked Threat Fox, and I checked for Pulses in OTX, but there wasn’t anything listed for these additional domains.
Will these additional domains be weaponized as Keitaro TDS domains for TA569 (SocGholish)? Looking forward to monitoring!
IOCs:
brickedpack[.]com
blacksaltys[.]com
losttwister[.]com
packedbrick[.]com
promiseresolverdev[.]com
IoFAs:
variablescopetool[.]com
apivuecomponent[.]com
loopconstruct[.]com
fetchdataajax[.]com
apistateupdater[.]com
objmapper[.]com