Table of Contents
TL;DR / Summary Up Front
ALOHA! This shows how you can take WatchingRac‘s post, create a profile of the delivery behavior, and search YouTube for slight variations to find other similar malicious videos.
Tactical Pause
THE CONTENT, VIEWS, AND OPINIONS EXPRESSED ON THIS DOCUMENT ARE MY OWN AND DO NOT REFLECT THOSE OF MY EMPLOYER OR ANY AFFILIATED ORGANIZATIONS. ALL RESEARCH, ANALYSIS, AND WRITING ARE CONDUCTED ON MY PERSONAL TIME AND USING MY OWN PERSONALLY-ACQUIRED RESOURCES. ANY REFERENCES, TOOLS, OR SOFTWARE MENTIONED HERE ARE LIKEWISE USED INDEPENDENTLY AND ARE NOT ASSOCIATED WITH, ENDORSED, OR FUNDED BY MY EMPLOYER.
Starting Source
Earlier this month I saw WatchinRac‘s post showing how YouTube videos had links to Lumma Stealer masquerading as video game cheats.
Here’s a snip of the post.

This is WatchingRac’s link for the YouTube search:

This is generally what the video info looks like:

It is a YouTube search for the unneutered version of hXXps[:]//www.mediafire[.]com/folder/7l9hjs0nu3sou/BorgHack. It is good, but I’ve got a hypothesis that there will be others if we scope it back to just hXXps[:]//www.mediafire[.]com/folder/. I wonder if we can take this post, and profile it to find other videos and other variations.
Dork 1 – MediaFire – Username
Here is my first YouTube dork:
https://www.youtube.com/results?search_query=https%3A%2F%2Fwww.mediafire.com%2Ffolder%2F

On a quick skim, it returns videos these two payloads in the description:
hXXps[:]//www.mediafire[.]com/folder/0s4l0ql101w6f/ROBLOX+EXECUTOR
hXXps[:]//mediafire[.]com/folder/nhf06saimhgzg/Aquantia
For each lure theme, at first it looked like one YouTube account amplified just one type of lure (ROBLOX, LOL, etc). I later observed some accounts had videos that were targeting different games with different payload URLs.
Dork 2 – MediaFire + Cheat
This is a better search because it specifies it must have cheat as a keyword:
https://www.youtube.com/results?search_query=https%3A%2F%2Fwww.mediafire.com%2Ffolder%2F+cheat
Here’s a snip showing it returns results that are old, but also a result from 6 hours prior to the time I checked.

Dork 3 – Google Sites + Cheat + Hack
MediaFire isn’t the only provider. I’ve also observed links to telegra.ph and sites.google.com. With those two, they host an article that includes a download link to the MediaFire source.
https://www.youtube.com/results?search_query=sites.google.com+cheat+hack&sp=CAI%253D
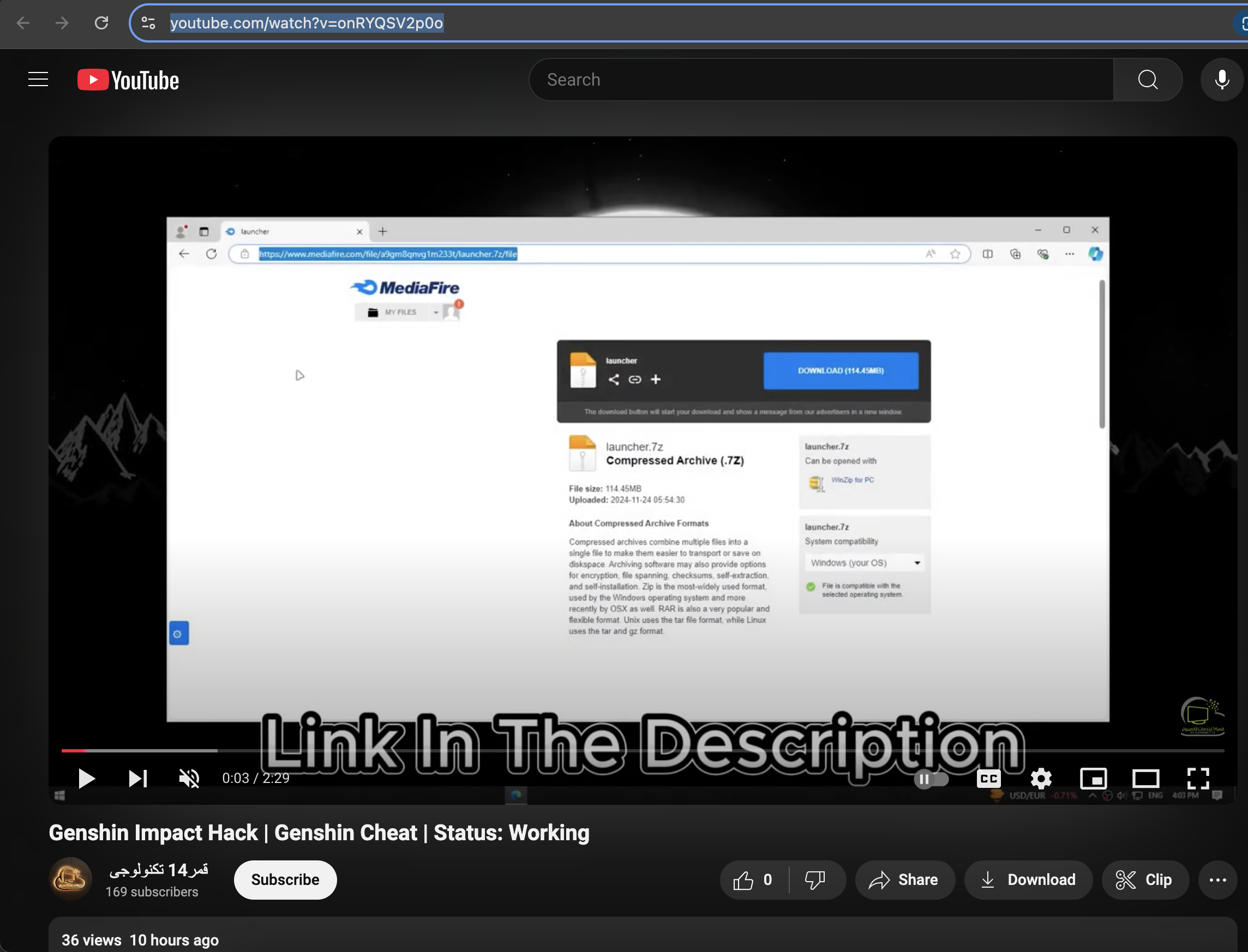
sites.google.com cheat hack
https[:]//www.youtube[.]com/watch?v=onRYQSV2p0o


Here’s the Any Run session:
https://app.any.run/tasks/52661105-1069-4d18-9992-d562b479dd27

It uses the Media Fire URL:
https[:]//app.mediafire[.]com/ig8zv39twapt2
It serves a link for a file that is large, but the executable is just a 450KB file shown here:
https://www.virustotal.com/gui/file/505a6196ef55cdf6ea05981ff1a1e92de468e7dde04b38a4f6e1747cb84f3d89

Dork 4 – HTTP + Cheat + Hack
Working pivot: https://www.youtube.com/results?search_query=https%3A%2F%2F+cheat+hack&sp=CAI%253D
https:// cheat hack
This returned results that were from 7 hours prior.

Dork 5 – Archive code: + Cheat
This dork searches for the “Archive code:” string that lists the password, and “cheat”.
Here’s the pivot: https://www.youtube.com/results?search_query=Archive+code%3A+cheat&sp=CAASAhAB
Archive code: cheat
It returned a result from 2 hours prior with 0 views.

I noticed there are slight variations in the steps. hXXps[:]//www.youtube[.]com/watch?v=4yPyNNaLSG8 has a slightly different value for step 2. Where it is normally “2. Disable Defender Anti-Virus”, the variation is “2. Off Defender Anti-Virus”

Dedicated Sites
While I was trying different search strings, I found some recent results that have dedicated sites (not free hosting like Google sites or MediaFire) as seen here:
https[:]//www.youtube[.]com/watch?v=IPfABaM2EGg
Here’s a snip of the vid, you can see the tell (password protected zip with the year)


Interestingly, they show how it is behind Cloudflare:

Here is an Any Run session showing the site. The password-protected archive theme appears to be common with Lumma Stealer.
https://app.any.run/tasks/98b54763-f7c2-4572-8ca5-4980247816f0

MediaFire File Updates
The threat actor updates the file uploaded to MediaFire. On 26NOV24 I ran the following YouTube dork:
https://www.youtube.com/results?search_query=https%3A%2F%2Fwww.mediafire.com%2Ffolder%2F
I observed this result:
https[:]//www.youtube[.]com/watch?v=rv3WYoCY-R4

Here’s the Any Run session for that:
https://app.any.run/tasks/a6398b98-56d1-4345-9bd2-9d1dabd076c7
The MediaFire URL is below:
hxxps[:]//www.mediafire[.]com/folder/vujkchz1ljjq6/loader
See below for the VT results for the Lumma Stealer included in the archive.
https://www.virustotal.com/gui/file/5fc50f2633274a7ee4446a7ba805aa1951b55e37b996865cddd7b23d5c2c852e

On 27NOV24, I redownloaded it via this Any Run session:
https://app.any.run/tasks/de0842ed-b45a-4cb3-9762-0b769e83c315
This is the same MediaFire URL: hxxps[:]//www.mediafire[.]com/folder/vujkchz1ljjq6/loader
The hash for the loader.exe changed to 944c924d8c27bd94a3885f78db1789c09cc0dc57d1d939fd5bbb9622873bce04. See below for the VT results. At the time of research, it did not return any results.

Summary
This shows how you can take WatchingRac‘s post, create a profile of the delivery behavior, and search YouTube for slight variations to find other similar malicious videos.
ALOHAZ!
IOCs
944c924d8c27bd94a3885f78db1789c09cc0dc57d1d939fd5bbb9622873bce04
5fc50f2633274a7ee4446a7ba805aa1951b55e37b996865cddd7b23d5c2c852e
https[:]//app.mediafire[.]com/ig8zv39twapt2
hxxps[:]//www.mediafire[.]com/folder/vujkchz1ljjq6/loader
hXXps[:]//www.mediafire[.]com/folder/0s4l0ql101w6f/ROBLOX+EXECUTOR
hXXps[:]//mediafire[.]com/folder/nhf06saimhgzg/Aquantia
https[:]//www.youtube[.]com/watch?v=rv3WYoCY-R4
https[:]//www.youtube[.]com/watch?v=IPfABaM2EGg
https[:]//www.youtube[.]com/watch?v=onRYQSV2p0o