Table of Contents
TL;DR
I saw a post on X that inspired me to search Shodan. I found an open directory associated with APT-C-35 (attribution based on file hashes that were listed in a Check Point report) and I was able to use a cool pivot for the first time.
Personal Disclaimer
THE CONTENT, VIEWS, AND OPINIONS EXPRESSED ON THIS DOCUMENT ARE MY OWN AND DO NOT REFLECT THOSE OF MY EMPLOYER OR ANY AFFILIATED ORGANIZATIONS. ALL RESEARCH, ANALYSIS, AND WRITING ARE CONDUCTED ON MY PERSONAL TIME AND USING MY OWN PERSONALLY-ACQUIRED RESOURCES. ANY REFERENCES, TOOLS, OR SOFTWARE MENTIONED HERE ARE LIKEWISE USED INDEPENDENTLY AND ARE NOT ASSOCIATED WITH, ENDORSED, OR FUNDED BY MY EMPLOYER.
Summary Up Front
I queried Shodan for “payload.exe” in the http.html value, and found a result for support-microsofthelp.com. Check Point attributed payload.exe to APT-C-35. I also found abc.exe in support-microsofthelp.com’s open directory. I ran it in Any Run, and it beaconed out to play-googyle.com. I pivoted on the WHOIS Registrant Email for play-googyle.com in Validin and found the email was also used to register mailservicess.com. I searched urlscan and found mailservicess.com previously served up.exe. Check Point also attributed up.exe to APT-C-35 in the same report. Finally, p.php on support-microsofthelp.com is an empty C2 panel that looks the same as the panel in the Check Point report. This endeavor was because I saw a post on X from Karol Paciorek.
Start
I was doom-scrolling X when I saw a cool post from Karol Paciorek. Here’s the post link and snip:
https://twitter.com/karol_paciorek/status/1859954097908256877

It reminded me of a blog I read from Matthew (https://x.com/embee_research) here: https://censys.com/a-beginners-guide-to-hunting-open-directories/.
Every time I see a post about finding malware in an open directory, I try to see if I can find similar results. I normally spend a few hours with no valuable results. This time I had just a bit of success. I wasn’t first to find anything, but I still thought it was cool to find interesting open directories.
Searching Shodan’s “http.html” Field
To start, I tried searching http.html. I learned you could do this after watching one of Chris Duggan’s videos. I tried a bunch of things, but payload.exe gave the first good result. Note the domain support-microsofthelp.com under the HTML title in the search result below. This is promising.

Here’s a snip of the head of the raw http.html results below.
https://www.shodan.io/host/179.43.141.89/raw#443

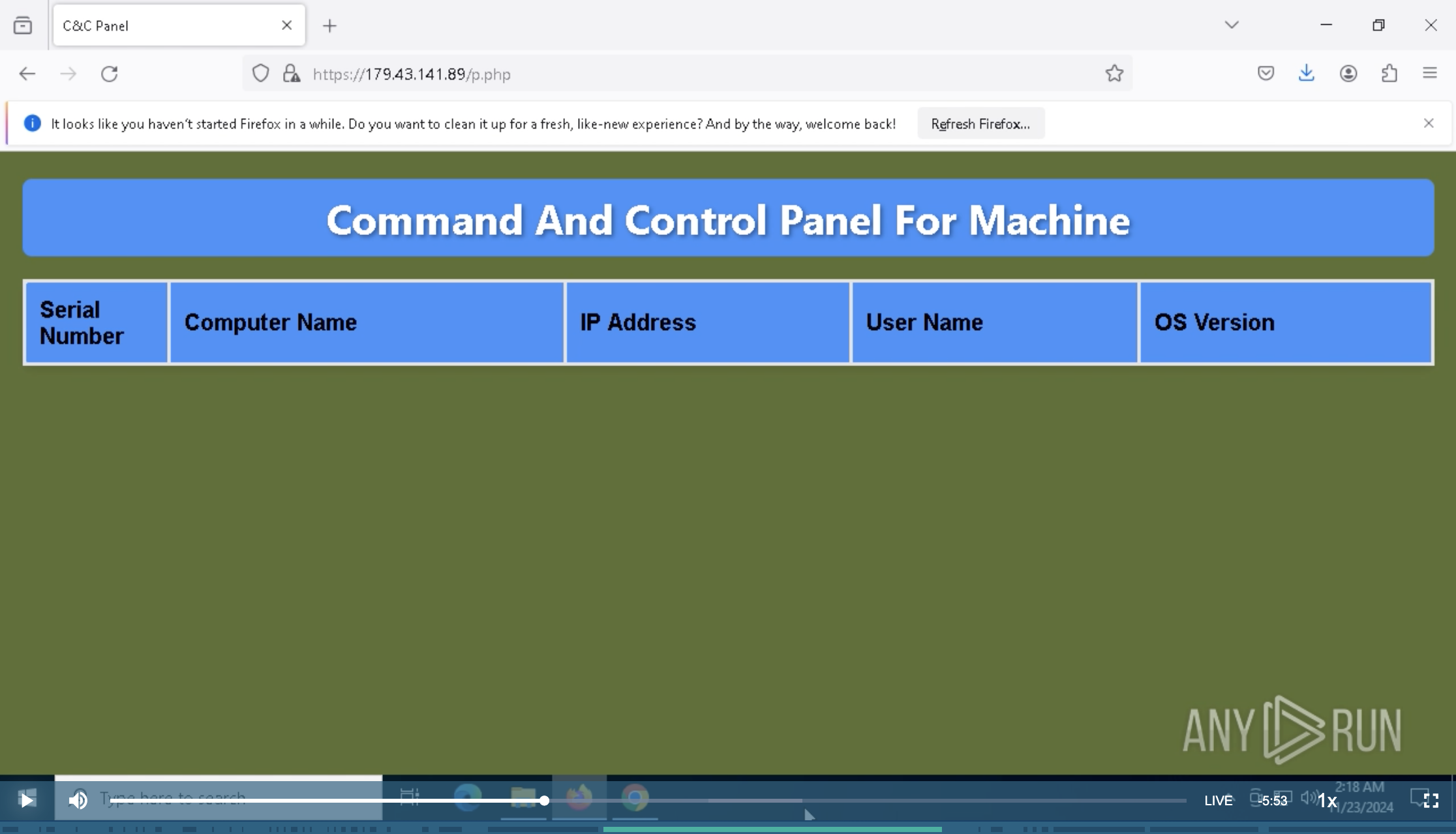
Accessing in Any Run
I accessed the IP via this Any Run session: https://app.any.run/tasks/b533cdb8-6b7e-4338-801b-1c9ecc376c1f.
The resource p.php appeared to be an empty C2 panel.

VirusTotal and Check Point Report
The two files listed below were already in VT. See the VT links below.
abc.exe:
https://www.virustotal.com/gui/file/522c13c5a1b5d176d21f9590dd649fb0b621eeaea9ad580e460724ceda4b954a
payload.exe:
https://www.virustotal.com/gui/file/3e9a60d5f6174bb1f1c973e9466f3e70c74c771043ee00688e50cac5e8efe185
Also, the comments for payload.exe here: state it’s listed in a report here: https://research.checkpoint.com/2024/foxit-pdf-flawed-design-exploitation/.

I reviewed the report. I should’ve read this earlier. Honestly, and sadly, I didn’t read the article until I was finishing up this draft. Check Point has the payload.exe SHA256 listed as “APT-C-35 / DoNot Team Downloaded1”.

Interestingly, Check Point’s Figure 5 shows a working snip of the C2 panel that looks like what I saw for p.php.

Anomalous Network Traffic Analysis
I observed abc.exe made a connection to play-googyle.com.

I downloaded the PCAP and SSL Keys from the session. I’ve pasted a snip of the stream below.

There are a few anomalous things that stand out.
- index.php is in what appears to be a random directory.
- I would assume this means if they were running operations using another domain, the directory might be custom – so it wouldn’t be something to use to search for matching patterns.
- The Referer value is the Any Run computer name.
- The Content-Type value ends with “—-qwerty”.
- This appears like something unique that could be used for detections.
- The User-Agent is “-“, and this could be a unique value to use for detections.
- The Host value isn’t the first line right after the HTTP method.
- RFC 7230 Section 5.4 states the Host field should be the first line following the request-line.
- The host play-googyle.com appears to attempt to masquerade as a Google Play domain.
- The qwerty form data includes key names that could be used for detections.
- The server response Content-Type value is not a common MIME type, and could be used for detections.
Here’s the contents of “DESKTOP-JGLLJLD.txt” viewed from Any Run:

Pivot on play-googyle
For play-googyle.com, I checked Silent Push to see if anything useful could be gleaned.
I enriched the IP in Silent Push. It looks like this IP may have previously been used in a Microsoft-themed scam with microsoftonlinerr.com.

Interestingly, the Registrant Email is not hidden.


I searched Validin to see if there were any related domains registered using this email address. The snip below shows that mailservicess.com also used the noraramly30121982 email address.

Research into mailservicess
I checked urlscan for scans related to mailservicess.com, and observed the interesting results shown in the snip below.
https://urlscan.io/search/#mailservicess.com

I selected the scan result linked below, and observed the snip below.
https://urlscan.io/result/3550f465-a560-4a5e-87d4-6ce7de46873b

I clicked the Lookup dropdown and pivoted to VirusTotal. It shows 50/72 vendors flagged it. View the interesting comment linked and snipped below.

The snip above is interesting because it is in the same Check Point report. Check Point has it listed as “APT-C-35 /DoNot Team Uploader”.

This is great. It validates that it was a good pivot. I will make a mental note to periodically check back on these registrant email addresses to see if there’s any new infrastructure registered.
I could probably continue attempting pivots on things like URI paths, additional filenames, and such. Every time I start writing about something I’m researching, I have issues with figuring out the best point to stop. I’ve got a bajillion pages in my research OneNote of things that I think are cool, but I couldn’t figure out when to stop and finalize, so they’re just a bunch of discontinued drafts that I commit to memory, but I don’t post them. It’s time to summarize this and close.
Summary
I queried Shodan for “payload.exe” in the http.html value, and found a result for support-microsofthelp.com. Check Point attributed payload.exe to APT-C-35. I found abc.exe on support-microsofthelp.com’s open directory. I ran it in Any Run, and it beaconed out to play-googyle.com. I pivoted on the WHOIS Registrant Email for play-googyle.com in Validin and found the email was also used to register mailservicess.com. I searched urlscan and found mailservicess.com previously served up.exe. Check Point also attributed up.exe to APT-C-35 in the same report. Finally, p.php on support-microsofthelp.com is an empty C2 panel that looks the same as the panel in the Check Point report. This endeavor was because I saw a post on X from Karol Paciorek.
ALOHAZ!
IOCs
support-microsofthelp.com
play-googyle.com
mailservicess.com
I limited the IOCs above to IOCs that I uncovered through my own research actions. For more IOCs, you can check out the Check Point report here: https://research.checkpoint.com/2024/foxit-pdf-flawed-design-exploitation/.
HANA HOU – other stuff
This section shows some things I looked up during this research endeavor. The results did not provide anything useful. I removed these parts from the upper part of this document during a review. I removed it because it sort of took away from the focus, and sort of made the document longer than it needed to be. While it didn’t provide anything directly related, I think it still adds value because it shows a sort of “behind the scenes” of things I check during research. Some of the parts below could be researched further – for example, the masquerading domains.
Here’s a snip of the support-microsofthelp.com enrichment in Silent Push.

I tried to enrich the IP to check the domain density, but there wasn’t anything useful.

I used the Domain Impersonation search and found some interesting domains that might not be related, but should definitely be investigated later!

Interestingly, the registrant email isn’t private.


I couldn’t figure out how to search for it in Silent Push, so I had to use Validin. A search on the registrant email did not return any new results.

Here’s the Domain Impersonation search for play-googyle.com and some results that I thought was interesting.