There’s a 7-Zip-masquerading site that is serving NetSupport Rat. I’ve been monitoring for a new 7-Zip FakeApp for a little over a week. This quick post shows how I became aware of it, and how easy it is to analyze it.
02APR25 UPDATE: Adding the sauce for the Silent Push query. I’m working on a project and need to reference the pivot techniques, so here it is. The pivot is the page title equals “Download”, the favicon hash, and and the string “getIPAddres” in the JS. There you go!

THE CONTENT, VIEWS, AND OPINIONS EXPRESSED ON THIS DOCUMENT ARE MY OWN AND DO NOT REFLECT THOSE OF MY EMPLOYER OR ANY AFFILIATED ORGANIZATIONS. ALL RESEARCH, ANALYSIS, AND WRITING ARE CONDUCTED ON MY PERSONAL TIME AND USING MY OWN PERSONALLY-ACQUIRED RESOURCES. ANY REFERENCES, TOOLS, OR SOFTWARE MENTIONED HERE ARE LIKEWISE USED INDEPENDENTLY AND ARE NOT ASSOCIATED WITH, ENDORSED, OR FUNDED BY MY EMPLOYER.
I initially learned of this when @crep1x’s initial post showed up in the feed. It talks about the 7-zip-masquerading sites serving NetSupport Rat. Here’s his post below.
https://x.com/crep1x/status/1850965395114508452

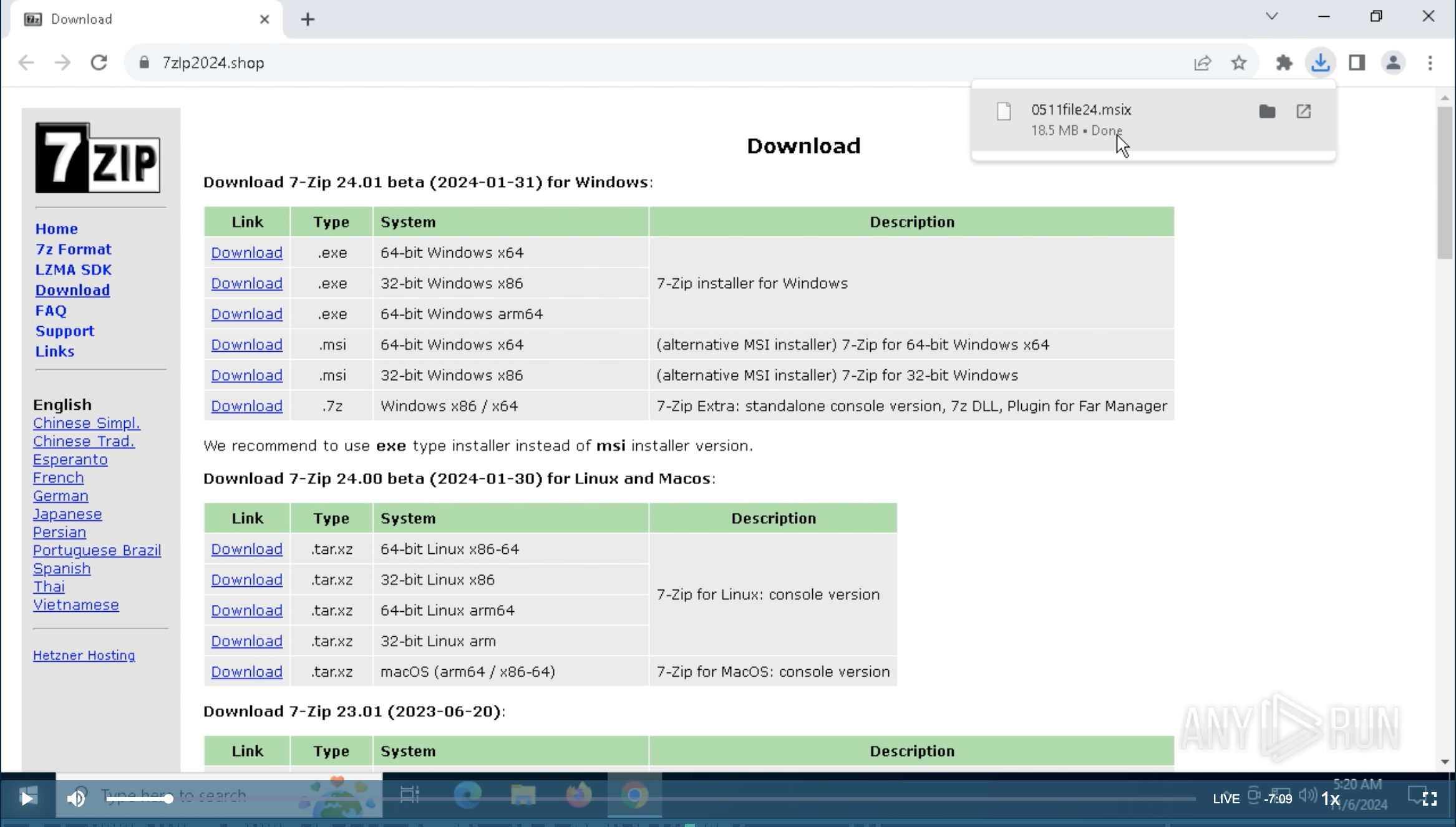
I created a Silent Push Web Scanner query to monitor for new domains, and I’ve been periodically checking it. I checked yesterday and observed the new domain 7zlp2024[.]shop as seen in the snip below.

I navigated to the site in Any Run. You can watch the video and see the full analysis here: https://app.any.run/tasks/d7975614-4156-4fda-bd25-c2f28f9c8e90
I clicked the Download link. All the links serve the same file, so it doesn’t matter which one you click.

The Any Run VM can’t run the MSIX file, so you’ll have to rename it to ZIP and extract it.

You’ll have to view the config.json file to figure out what is supposed to happen when the MSIX file is ran. I didn’t view it in the Any Run session because I’m already familiar with this one, but here’s a snip of the of the file viewed from the Any Run viewer (reviewed after the session). It uses PsfRunDll64.exe to run sofgnarfoj.ps1.

I viewed it in the session so that I could run it and extract the NSR configs. I only copied and ran lines 2-4, from the snip below, in PowerShell.

After running the PS code to extract the encrypted payloads, you can first view NSM.LIC file. It will show the licensee and serial_no values that you can use for tracking purposes (thanks Randy!).

Next, you can view the client32.ini file to view the GatewayAddress (C2 IP).

There you have it! Here’s the fruits of the labor below!
https[:]//7zlp2024[.]shop >> 0511file24.msix (b3a95ec7b1e7e73ba59d3e7005950784d2651fcd2b0e8f24fa665f89a7404a56)
MGJFFRT466
NSM301071
62.76.234[.]49:443